![[SMART MOCKUP] [GUIDES] [KPI GUIDE WITH BACKGROUND] [SMART MOCKUP] [GUIDES] [KPI GUIDE WITH BACKGROUND]](https://elimity.com/hubfs/%5BSMART%20MOCKUP%5D%20%5BGUIDES%5D%20%5BKPI%20GUIDE%20WITH%20BACKGROUND%5D%20%20.png)
The Essential KPIs to Achieve IAM Success
Identifying IAM inefficiencies remains a challenge for organisations with numerous applications and valuable data.
Our guide walks you through everything you need
to start using KPIs to improve your IAM security.
✅ 8 Essential KPIs
✅ Based on ISO27001 framework
✅ Increasing IAM Effectiveness
How Customer GEOxyz Took Control Over User Access
The 8 Identity Security Controls for NIS2-Compliance
Having provable control over who can access which data in such an environment is crucial for NIS2 compliance.
✅ 8 Must-Have Controls
✅ Report on Your Users and Their Accesses
✅ Based on NIS2-Framework
Customer Cases
Guides
How to Build Your Identity Data Fabric
✅ Why more tools create blind spots
✅ 4 steps to full IAM visibility
✅ Based on NIS2 & ISO27001
Risk-Driven Approach to IAM
✅ Top 12 IAM risks by category
✅ Build Your IAM Risk Matrix
✅ Based on ISO 27001 & NIS2
Build The Perfect Risk Cockpit for Active Directory
![[SMART MOCKUP] [GUIDES] [How To Build The Perfect Risk Cockpit for Microsoft Active Directory]](https://elimity.com/hs-fs/hubfs/%5BSMART%20MOCKUP%5D%20%5BGUIDES%5D%20%5BHow%20To%20Build%20The%20%20Perfect%20Risk%20Cockpit%20for%20Microsoft%20Active%20Directory%5D.png?width=284&height=284&name=%5BSMART%20MOCKUP%5D%20%5BGUIDES%5D%20%5BHow%20To%20Build%20The%20%20Perfect%20Risk%20Cockpit%20for%20Microsoft%20Active%20Directory%5D.png)
✅ What is an IAM Risk Cockpit?
✅ The 8 Key Controls for Active Directory
✅ Based on the ISO 27001 Framework
Better Together: How IVIP Complements IGA

✅ How the Combination Works in Practice
✅ Achieve Intelligent Compliance
IAM from a CISO's Perspective
![[SMART MOCKUP] [GUIDES] [IAM FROM A CISOS PERSPECTIVE]](https://elimity.com/hs-fs/hubfs/%5BSMART%20MOCKUP%5D%20%5BGUIDES%5D%20%5BIAM%20FROM%20A%20CISOS%20PERSPECTIVE%5D.png?width=1080&height=1080&name=%5BSMART%20MOCKUP%5D%20%5BGUIDES%5D%20%5BIAM%20FROM%20A%20CISOS%20PERSPECTIVE%5D.png) ✅ Learn why should you care about IAM
✅ Learn why should you care about IAM
✅ Master the three major disciplines of IAM
✅ Must-do's for securing IAM
Prove that you are in control with Elimity's Key Identity Data Indicator Canvas ![[SMART MOCKUP] [GUIDES] [KEY INDICATOR CANVAS]](https://elimity.com/hs-fs/hubfs/%5BSMART%20MOCKUP%5D%20%5BGUIDES%5D%20%5BKEY%20INDICATOR%20CANVAS%5D.png?width=1080&height=1080&name=%5BSMART%20MOCKUP%5D%20%5BGUIDES%5D%20%5BKEY%20INDICATOR%20CANVAS%5D.png)
👉 Interactieve Datasheet
👉 Overview of the key identity indicators
👉 Calculate your security score
Videos
Why Identity Data Analytics is Key to Strong Security Posture
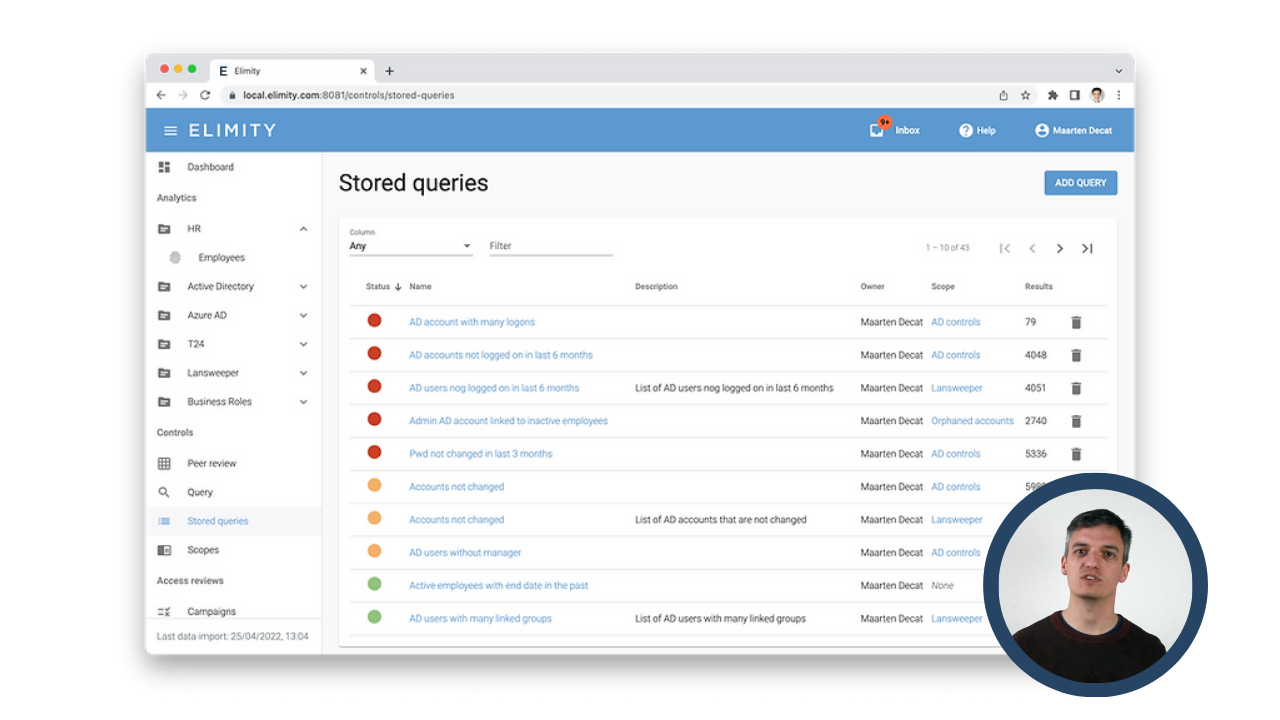
✅ Identity Data KPIs
✅ How to Achieve Identity Data Insights
✅ Customer Cases: Impact of Analytics
What is Light IGA?

✅ IGA light vs IGA
✅ Key Features of IGA Light
✅ Case Study: Control User Access
How to prove that you are in control?
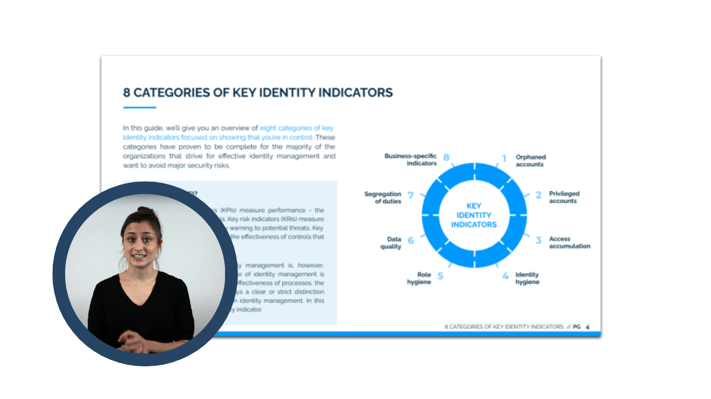
✅ Why do you need Identity KPIs
✅ 8 Crucial Identity Data KPI
✅ How to Achieve Identity Data Insights
Take Control of Your Users and Their Accesses

![[SMART MOCKUP] [GUIDES] [NIS2 GUIDE WITHOUT BACKGROUND]](https://elimity.com/hubfs/%5BSMART%20MOCKUP%5D%20%5BGUIDES%5D%20%5BNIS2%20GUIDE%20WITHOUT%20BACKGROUND%5D%20%20.png)






![[SMART MOCKUP] [GUIDES] [SOLUTION BRIEF]](https://elimity.com/hubfs/%5BSMART%20MOCKUP%5D%20%5BGUIDES%5D%20%5BSOLUTION%20BRIEF%5D%20%20.png)

.png?width=940&height=788&name=SMART%20MOCKUP%20-%20IDENTITY%20SECURITY%20REPORT%20(1).png)
![[SMART MOCKUP] [GUIDES] [KPI GUIDE WITHOUT BACKGROUND] (2)](https://elimity.com/hs-fs/hubfs/%5BSMART%20MOCKUP%5D%20%5BGUIDES%5D%20%5BKPI%20GUIDE%20WITHOUT%20BACKGROUND%5D%20(2).png?width=1080&height=1080&name=%5BSMART%20MOCKUP%5D%20%5BGUIDES%5D%20%5BKPI%20GUIDE%20WITHOUT%20BACKGROUND%5D%20(2).png) ✔ 8 Categories of identity indicators
✔ 8 Categories of identity indicators