When an organization does not have one central IAM solution, it becomes a challenge to have analytics at the global level. Waiting for a central, full-blown Identity and Access Management (IAM) solution is not an option.

Elimity Insights is a simple solution that allows you to collect information and slice and dice it across many sources of information. I have never encountered another tool that can provide you with that many insights in just three to four days.

Challenges
❌ Complex Hybrid IT environment
❌ Highly Sensitive Information
❌ Heavily Regulated Financial Sector
5 Tips On Achieving Mature Access Governance Within Days
Securing access to data and applications has become a cornerstone of any modern cybersecurity strategy.
✅ Why do Identity and Access Management (IAM) projects often fail?
✅ The Essentials of Mature User Access Management
✅ Tips How You Can Control User Access With Minimal Effort

Key Results Customer Case
✅ No longer manual, large Excel spreadsheet
✅ 3 Days to achieve first visibility into users and their accounts
✅ Always-up-to-date comprehensive view of all IAM sources
✅ Business-friendly and automated access reviews for multiple stakeholders
✅ Automatic creation of tickets based on the changes requested in Elimity Insights
✅ Necessary audit proof for compliance with ISO27001
How we applied identity data analytics
- Deployed Elimity Insights platform
- Integrating with 10+ applications
- Linked all data, ensuring up-to-date identity data set
- Empowered IAM team with day-to-day analyses
- Advanced data insights
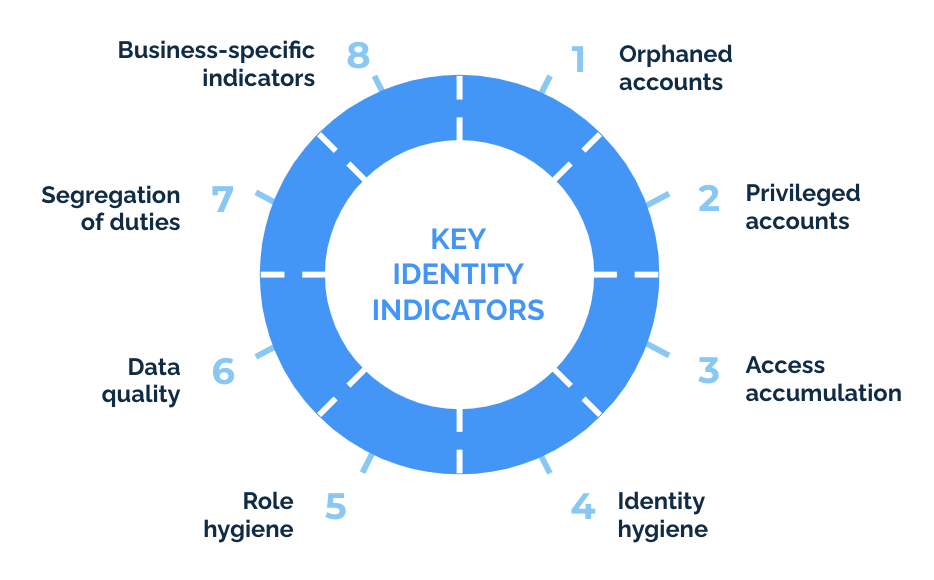
KPI-Driven approach to IAM
Our guide walks you through everything you need to start using KPIs to improve your IAM security.
Your Ultimate IGA-Deployment Checklist
Are you starting your identity governance and administration (IGA) journey? Follow Elimity's checklist for successful IGA deployment.
![CUSTOMER TESTIMONIAL [FEDERALE VERZEKERINGEN] - SMART MOCKUP CUSTOMER TESTIMONIAL [FEDERALE VERZEKERINGEN] - SMART MOCKUP](https://elimity.com/hs-fs/hubfs/CUSTOMER%20TESTIMONIAL%20%5BFEDERALE%20VERZEKERINGEN%5D%20-%20SMART%20MOCKUP.png?width=1200&height=1200&name=CUSTOMER%20TESTIMONIAL%20%5BFEDERALE%20VERZEKERINGEN%5D%20-%20SMART%20MOCKUP.png)

.png)