The 8 Identity Security Controls for NIS 2-Compliance ✅
Having provable control over who can access is crucial for NIS 2-Companies. Apply these KPIs today and become audit-ready!
![[SMART MOCKUP] [GUIDES] [NIS2 GUIDE WITHOUT BACKGROUND]](https://elimity.com/hs-fs/hubfs/%5BSMART%20MOCKUP%5D%20%5BGUIDES%5D%20%5BNIS2%20GUIDE%20WITHOUT%20BACKGROUND%5D%20%20.png?width=3375&height=3375&name=%5BSMART%20MOCKUP%5D%20%5BGUIDES%5D%20%5BNIS2%20GUIDE%20WITHOUT%20BACKGROUND%5D%20%20.png)
✅ 8 Essential Identity Security Controls
✅ Report on your users and access
✅ Based on NIS 2-Framework
Get the free guide!
Executive Summary
Over the past decades, many organizations have - rightfully so - introduced proper IAM to securely manage its ever increasing digital identities and their accesses. Still today, new challenges emerge and new layers are added. Hence, IAM systems should be continuously improved to meet today’s and tomorrow’s increasing demands. In practice identifying potential inefficiencies or gaps and measuring IAM effectiveness remain a challenge. Applying a KPI-driven approach to IAM is (one of) the solutions to identity areas for improvement as well as areas of success.
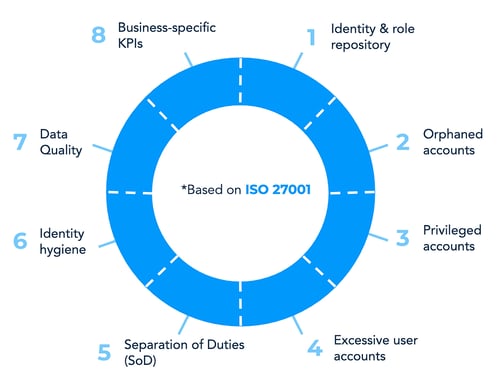
In this guide we bundled a comprehensive set of KPIs that have proven to be applicable to and complete for the majority of the organizations that strive for risk reduction and/or improvement of process and data quality. These KPIs are derived from the ISO 27001 based identity wheel which presents eight essential KPI sets.
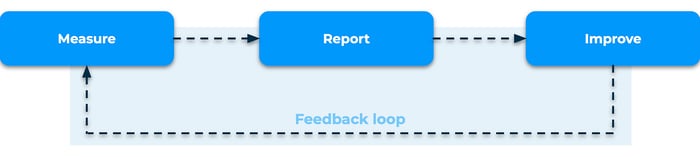
Don’t forget, however, that KPIs in itself are just KPIs. IAM effectiveness can only be improved if those KPIs are actually used to drive decisions, actions and their prioritization. The proposed closed-loop model, that consists of 3 steps - measure, report and improve - and a feedback loop, enables you to do exactly that.
Introduction
Over the last decade, regulatory and security demands have grown to challenging levels. Almost every company now has to manage a large number of applications within a complex IT infrastructure, consisting of numerous accounts and permissions. Having provable control over who can access which data in such an environment is crucial for NIS2 compliance, protecting privacy, and defending against cyber threats.
The answer to this challenge lies in establishing identity governance processes—for requesting, approving, and reviewing employees' access. These processes are critical for maintaining NIS2 compliance and operational efficiency, but they don’t necessarily ensure that you are truly in control of users and their access.
How do you know if you’re in control? And how can you prove it?
These questions are why we wrote this guide. Reporting on your identity security controls and identifying potential risks or gaps remains a significant challenge. Based on our experience and frameworks such as ISO 27001, we’ve compiled a set of crucial identity security controls you should measure to ensure you’re in control—and to prove that you are.
A word on terminology
- The words ‘entitlements’, ‘permissions’ and ‘privileges’ are used interchangeably throughout the text. Whichever of these is used depends on the IAM system that is deployed. Nevertheless, the meaning is similar.
- ‘Access rights’ should be understood as a collection of specific permissions that user accounts are entitled with directly or because they are assigned to one or more roles.
- The words ‘KPI’ and ‘metric’ are used interchangeably throughout the text. Even though it is often stated that a KPI consists of several specific metrics, we will not make that difference in this paper.
- The difference between a Key Performance Indicator (KPI) and a Key Risk Indicator (KRI) is what each of them measures. A KPI measures performance (i.e. the achievement of identified goals) while a KRI measures risk exposure (i.e. an early warning to identify a potential threat). One of the main goals of an IAM system is, however, reducing risk. As a result, there is not always a clear and strict line between a KPI and KRI within IAM.
- To avoid confusion, only the word ‘KPI’ will be used in this text. Remember, however, that this could also refer to an indicator that in fact measures risk exposure.
KPI-driven IAM
Example
In many organizations, the number of unassigned roles increases rapidly due to an ever changing access landscape. Once this is identified as an issue, whether for security or operational reasons, role managers should have the right information available to decide whether such an unassigned role is only temporary unassigned or whether it can be deleted.
The right choice of KPIs
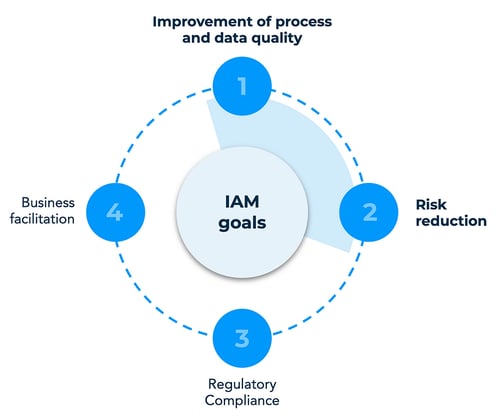
Which KPIs are relevant to measure and follow-up is derived from the overall IAM goals. In many organizations the main goal or combination of goals of IAM can differ. In strongly regulated organizations for example, regulatory compliance is obviously (one of) the main goal(s). Other commonly stated goals of IAM are risk reduction, improvement of process and data quality, and business facilitation. Even within an organization different people can be responsible for different goals of the IAM system. As a result, the relevant KPIs for each of these people will often slightly differ. Understanding who will use the KPIs and how is thus key to choose the right metrics. Certain KPIs can of course be relevant to measure the success of multiple goals at the same time.
Once the goal(s) are determined, you should ask yourself the following: “Which questions define the goal(s) more precisely?”.
The relevant metrics are then - often simply - the answers to those questions. By following this approach, the KPIs will be aligned with the IAM strategy and in turn contribute to the accomplishment of the goal(s).
It’s important, however, to understand that the choice of KPIs is not set in stone for all time. There are several factors that could influence the set of relevant KPIs. Think about strategies and goals that develop over time, more information that becomes available, changes in the regulatory landscape, etcetera. In order to continuously ensure that the right set of KPIs is measured, it should be revisited once in a while. Also note that there’s no ideal number of KPIs that you should have.
KPIs guide: risk reduction & improvement of process and data quality
We will cover KPIs particularly focused on the IAM goals risk reduction and improvement of process and data quality (see figure below). The KPIs related to business facilitation are more duration-based. Think about the average duration of employee readiness and the average duration of access request processing. Most of the KPIs measuring regulatory compliance are regulation-specific and dependent upon audits. Think about the number of compliance violations and the number of successful audits.
Identity wheel: KPI sets
In this chapter we bundled a comprehensive set of KPIs that have proven to be applicable to and complete for the majority of the organizations that strive for risk reduction and/or improvement of process and data quality. The ISO 27001 based identity wheel (see below) shows eight KPI sets, each entailing several specific KPIs.
These KPIs are listed on the following pages. Note that for the KPIs both the quantity and the distribution (e.g. across departments) can be interesting.
1. Identity & role repository
-
The number of users (per department or organizational unit, per manager, …)
-
The number of newly created users
-
The number of disabled users
-
The number of (organizational, container, IT, business, technical, …) roles
-
The number of entitlements
-
The number of applications integrated in the current IAM system
-
The number of roles relative to the number of departments
-
The number of IT roles relative to the number of business roles. This can, of course, be done for any type of roles of interest.
-
The number of entitlements relative to the number of users
-
The number of entitlements relative to the number of roles
Rule of thumb
What is the relation between the number of roles and users in your organization?
A rule of thumb regarding the number of roles in your IAM system: the total number of roles should be no more than 10% of the total number of users. In many organizations without proper role management this percentage is greatly exceeded. This represents an overly complex role model that is difficult to maintain and can lead to errors and operational inefficiencies.
2. Orphaned accounts
-
Users that have not logged in for quite some time. Accounts that have not been used for a certain period of time are also known as dormant accounts. What that time period should be exactly can differ between organizations. Nevertheless, 90 days is often considered the limit.
- For certain accounts, such as admin accounts, one might prefer a shorter time period compared to other accounts. Hence, this KPI can be split into several sub-KPIs.
-
Users that have never logged in.
-
Uncorrelated user accounts, also known as ghost accounts. These are accounts that are not linked to an active user or not linked to a user at all.
-
User accounts with a status indicating inactivity. What this status is exactly depends upon the IAM system that is used in the organization. Think for example about an employment status ‘retired’ or an activity status ‘inactive’. The clue is to look at the user characteristics in the IAM system that could indicate inactivity of a user.
3. Privileged accounts
Privileged accounts, generally defined as accounts that have significantly more access rights than ordinary accounts, exist in many forms and shapes. However, when not properly managed and monitored, privileged accounts pose significant security risks. These risks could come from all sides: malicious ‘outsiders’ (such as hackers), or careless or disgruntled ‘insiders’. Whoever gains access to these privileged accounts can control organization resources, access sensitive data, or even change or disable (security) systems.
It’s important to know how many and what kind of privileged accounts exist in the organization. Note, however, that some of the below mentioned types of privileged accounts can overlap. To start off, think about the following kinds of privileged accounts:
- Administrator accounts, think about Local Admin and Domain Admin.
- Stealthy accounts. These accounts are granted administrative privileges on one or more systems but often exist below the radar as they are not labeled ‘Admin’.
- Privileged service accounts such as Domain Service accounts.
- Non-personal accounts (NPA). These accounts are not directly related to a uniquely identifiable person/employee, nor are they the result of the 'joiner – mover - leaver' HR processes in an organization. Such accounts are often quite powerful (e.g. admin or root account) but difficult to detect. On top of that, login with the account doesn’t leave an audit trace showing which person has actually used it. In other words, there is not a specific person that can be held accountable.
- Privileged data user accounts. Even though these users are not typical privileged accounts, they should be considered privileged anyway, because of the sensitive data they can access. Think about the accountant who has access to financial data of his customers, an HR employee with access to sensitive employee data or a doctor who has access to patient information.
- Privileged role-based accounts. Depending on the role model, certain roles can be considered privileged. Therefore, we should consider users assigned to one or more of these roles as privileged accounts.
YOU CAN'T PROTECT WHAT YOU CAN'T SEE
4. Users with excessive access rights
The difference with privileged accounts and users with excessive access rights is that the former focuses on users who should have (many) sensitive access rights by definition while the latter focuses on users who accidentally have (too) many access rights.
One of the most important principles in information security is the principle of least privilege (PoLP). This principle is the practice of limiting access rights for users to the bare minimum they need to perform their intended work. It is a common misconception to only think about malicious employees when considering using the least privilege principle. The thing is that employees can also accidentally leak data due to phishing, a lost laptop, etc. But whether it's on purpose or not, the less data your employees can leak, the better.
It’s a fact that the cumulated access rights and permissions of all your users together determine the attack surface size of your organization, which of course should be kept as small as possible. Unfortunately, there’s often a gap between granted access rights and used access rights. This indicates that users have too many access rights, unnecessarily enlarging your attack surface
- Outliers. These can be defined as users that have more access rights (i.e. are assigned more roles or have more privileges) than their peers. Often this is the result of employees changing departments or functions without the former - and now unnecessary - access rights were deprovisioned.
- Another way of finding outliers is by comparing them to an ideal role-profile. Depending on the job function a certain employee has, a certain set of roles might be appropriate. This, however, is only applicable to organizations working with such role-profiles.
- Users assigned with a high number of roles or permissions. What is considered as ‘high’ depends on the role model and organizational context.
Rule of thumb
A rule of thumb about when a user can be identified as having a high number of roles or permissions: the total number of roles or permissions exceeds twice the average (see identity & role repository: the number of roles/permissions relative to the number of users).
5. Separation of Duties (SoD)
Separation of duties, also known as segregation of duties, is considered as one of the most difficult and often costly identity controls to implement properly. The objective is to disseminate the tasks and associated permissions among multiple people. That way it is much more difficult to commit fraud since at least two people must work together to do so. However, the objective is no longer limited to fraud prevention, but also includes security and privacy. If properly designed and implemented correctly SoD ensures that employees don’t have conflicting responsibilities or interests. For example, you don’t want the person defining a policy to have the ability to approve its execution.
Apart from the SoD controls itself, the metrics to see how you are doing:
- SoD violations. Besides the total number of SoD violations, it can also be interesting to look at the number of specific SoD violations to identify those toxic combinations that seem the hardest to resist. For these violations, a tactical clean-up will probably not do the trick. A strategic redesign (see info on the right), however, might improve the situation.
- Undecided access rights combinations. These are the combinations of roles, entitlements or applications for which it’s not clear whether they are considered ‘toxic’ or not. If such a combination occurs in practice, it’s important to know whether it’s allowed or not in order to take appropriate action (if required).
Remediation or mitigation?
Remediation: permanently delete the conflict. There are two options to achieve this:
- Tactical clean-up: revoke a group, delete the user account, …
- Strategic redesign: redesign certain groups or processes
Mitigation: accept the risk, but put controls into place to lower the risk. For example by lowering the impact by defining a max amount for an invoice without additional approval.
6. Identity hygiene
It is important to realize that identity hygiene (i.e. proper maintenance of the repository) and information security are strongly interconnected: a well-maintained IT environment is better protected against information security risks. Applying good practice to users, roles and entitlements not only helps to prevent risks, but it’s also a lot easier and needs considerably less effort compared with a situation where you periodically have to clean up the mess. In other words: prevention is better than cure.
Some metrics to measure how well you’re doing regarding user hygiene:
- Users that have no roles or entitlements assigned.
- Users that have no access to any applications.
- User accounts that have not been changed for a certain period of time. What that time period should be exactly can differ between organizations.
- User accounts with direct entitlements, not assigned through roles.
- Users accounts for testing purposes (i.e. test accounts).
- Users (and more specifically their access rights) that are not reviewed in a certain period of time. Again, what that time period should be exactly can differ between organizations and often depends on the frequency of (re)certification campaigns.
- This KPI can also be set up for specific types of accounts, such as admin accounts.
- In case the organization enforces a password expiration policy: user accounts with expired passwords.
Some metrics to measure role hygiene. Note that these KPIs can be split into sub-KPIs for specific types of roles such as IT or business roles:
- Roles that do not consist of other roles or entitlements, also known as empty roles.
- Roles that are not assigned to any user, also known as unassigned roles.
- Roles that are (not) reviewed in a certain period of time. Again, the exact time period depends on the frequency of (re)certification of roles in the organization.
- Roles with an additional approver.
Some metrics to measure entitlement hygiene:
- Entitlements that are (not) assigned via a role.
- Entitlements that are not assigned to any user.
- Entitlements with an additional approver.
7. Data quality
In order to get accurate results from all of the controls mentioned above, it’s crucial that all relevant data (‘attribute values’) are entered correctly. The KPIs will only reflect the actual state if the data in the IAM system is accurate, complete and up to date. Many of the processes such as onboarding, offboarding and in general changing data, are automated with the help of IAM systems. As a result, finding inaccuracies or blank fields is also an opportunity to improve these processes. Simply solving specific data issues without considering the root cause is like fighting a running battle.
GARBAGE IN IS GARBAGE OUT
There are many KPIs that help to measure this. Think about all the different data attributes in the IAM system that could be left blank. However, it’s important to focus effort on those attributes that are crucial for other KPIs or to take action to improve identified issues. Remember that more in-depth information and action-oriented insights are required to actually improve identified issues. Without the right information, it’s almost impossible to decide whether a certain user account or role can be disabled/revoked or not.
Some metrics that are essential for the majority of organizations:
- Users without a manager, department, or email.
- Roles without a (proper and clear) description or owner.
- Entitlements without a (proper and clear) description and owner.
- Applications without a (proper and clear) description and owner.
8. Business-specific KPIs
Next to the more general KPIs mentioned in the previous sets, it’s important to enhance these KPI sets with business-specific metrics. In financial institutions, for example, it’s often the case that an employee needs the proper certification/training to perform a certain action. Hence, the number of employees who do have the permissions to execute that action, but don’t have the proper certification could be such a business-specific KPIs. Another frequently seen situation is when companies focus on security awareness training and want to measure for whom such training has been too long, especially if these users have a lot of privileges.
Closed-loop model
Obviously, KPIs in itself are just KPIs. IAM effectiveness can only be improved if those KPIs are actually used to drive decisions, actions and their prioritization. Following the closed-loop model, shown below, will enable you to do exactly that.
Moreover, remember that in order to maximize the value of your existing IAM system, it’s crucial to know (1) where you are now, (2) where you are going and (3) where you want to be. Combining those three will enable you to timely identify areas for improvement so as to ensure effective and efficient IAM.
Measure
All organizations could benefit from a metrics-based approach to IAM. Measuring performance is crucial to make timely and informed decisions about short and long term activity focused on increasing the ROI of IAM. It provides hard evidence - numbers don’t lie if calculated correctly - that can support decision making, create awareness and simply help you to make your case. On top of that, KPIs allow you to benchmark against peers in order to understand the relative IAM performance. It enables you to understand whether the total number of roles in your type of organization (industry, size, etc.) is below or above average, for instance.
Moreover, depending upon the goals of IAM in the organization and the specific IAM responsibilities of someone, not only the type of KPIs (see The right choice of KPIs) but also the importance of those right KPIs will differ. Hence, it’s important to assign ‘weights’ to the sets of KPIs or specific KPIs in order to focus efforts and get a correct image of the IAM system’s effectiveness. It could, for example, be possible that empty roles are prominent in the organization, but that they are not a priority right now. Ensuring that the focus is correctly distributed across the different KPIs enables you to set up a long-term, focused plan.
Report
Just measuring KPIs will not enable you to get the most out of your IAM system. Reporting about those KPIs, however, provides context which allows to better understand where you are now and identify areas of success and areas to improve in order to get where you want to go. For that reason, it’s important to look at the KPIs over time in order to detect trends and correlations. Imagine, for example, that the number of roles has been steadily increasing over time and that the same trend can be seen with unused roles (e.g. unassigned or empty roles). In that case, evaluating those unused roles - and deciding whether they can be deleted - could help to avoid a ‘role bloat’.
Unfortunately, the majority of applications that are currently being used for reporting about IAM KPIs are not specifically built for it. A common ‘gap’ is that you can only see the numbers of the KPIs but not what’s behind it. It is possible to see that there are for example 100 unassigned roles, but it’s not possible to click through to find out which roles are involved.
Improve
Being KPI-driven is only as valuable as the value of the actions that result from it. Hence, I can only suggest using KPIs to drive prioritization of both the most valuable short term and long term activities and investments.
There are several activities in which you can maximize the value of IAM for your organization. An obvious one: clean-up. We’ve already talked about cleaning up roles to avoid a ‘role bloat’. Besides unassigned and empty roles, think about cleaning up incorrect access rights and inactive accounts. Also here prioritization is key. Which issues to clean up first depends on the relative importance and current state of the corresponding KPIs. It’s important to remember that a ‘clean’ identity and role repository makes identity management a lot more manageable.
Moreover, it’s not only important to clean up identified issues but also to find out whether there is a bigger root cause that can be solved. Think about ‘joiner - mover - leaver’ HR processes that should be updated.
Feedback loop
Once actions are taken, this will - hopefully - be reflected in the KPIs. Tracking progress enables you to evaluate the success of a certain activity in improving IAM effectiveness. Those experiences and knowledge allows for better prioritization of next actions. It’s a process of continuous improvement. Not only focused on the output but also on the means of getting there.
Conclusion
Using key metrics does not only enable an organization to understand how its existing IAM system is performing but also helps to better plan for maximizing its value for the organization. It’s crucial - now more than ever - to understand what is needed to increase the success of these solutions to ensure efficient and secure management of all identities and their accesses.
Main takeaways:
-
Measure how you are doing. Choose a set of KPIs based on the organization’s IAM goals and your specific responsibility within IAM. But remember that KPIs in itself are just KPIs.
-
Report on KPIs over time in order to detect trends and areas for improvement. Allow for dynamic reporting that can actually be used by various stakeholders.
-
Improve the current state by cleaning up accounts, roles, entitlements and other objects that don’t belong in the identity repository anymore.
-
Track progress over time and learn continuously.