Enterprise-wide visibility and monitoring of users and their accesses
For our client, a government organization with a complex IT environment, Elimity improved their cyber security posture with identity intelligence.
👉 Over 160.000 users and accesses
👉 Time-to-Value: 2 weeks
👉 Result: complete overview IAM
💡ENTERPRISE WIDE VISIBILITY?
For our client, a government organization with a complex IT environment, proper control of user accesses is a crucial part of the cyber security strategy.
Obtaining an enterprise-wide view of the accesses was, however, not feasible with the current identity management suite, SAP IdM, that only offers basic reporting capabilities.
We helped our client by setting up an enterprise-wide view of more than 160,000 users and their accesses, including automated monitoring, in just 2 weeks of work. This enabled the cyber security team to improve their understanding of their current user accesses, their IT risk posture, and the evolution of those across multiple applications.
RESULT
By putting their identity data to work and tailoring the control sets to their needs, we helped our client's cyber security team to create a continuous assessment of the situation, a continuous state of control.
IMPACT
In addition, they could now use Elimity’s platform to report on the progress that they were making and leave Excel behind, improving the understanding and engagement of other stakeholders such as management.
APPROACH
Three step approach to gain complete visibility in your enterprise-wide users and assets.
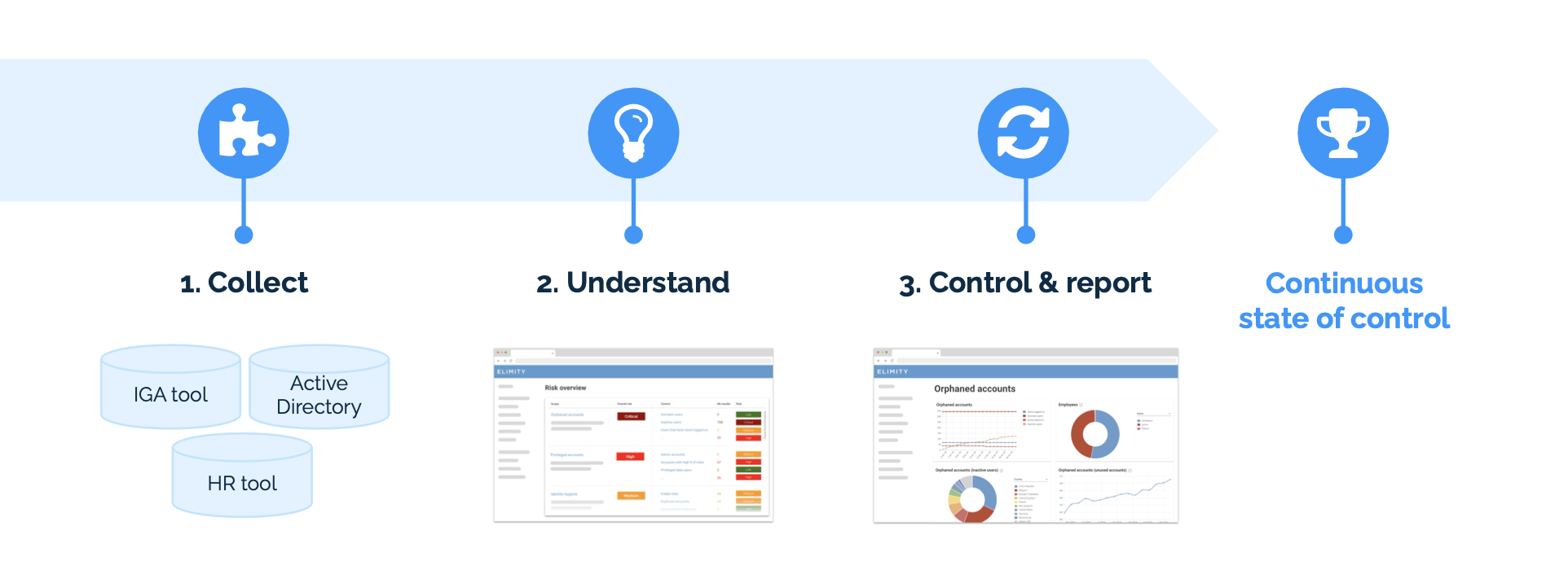
1. Collect
Together with the client we started this project with identifying the systems in which most of the relevant identity data resides. For the purpose of understanding the IT risk posture, that turned out to be the main IGA tool (SAP IdM), Active Directory and the HR system. We assisted our client in setting up a mature IAM data mart, including automated data collection and consolidation. This was fundamental to obtaining a comprehensive view of the identities, their accesses and the associated risks.
2. Understand
We provided the cyber security team with a self-service intelligence platform specifically for identity data. Out-of-the-box control sets enabled them to get a first impression of the organization’s identity risk posture immediately. Of course, every organization is different and as such we assisted them to modify some of the controls and KPIs as well as to create new ones. That resulted in control sets that were tailored to their needs. Additionally, extensive analytics and visualizations enabled them to dig into the details and really understand the nature of the risks.
Besides understanding the IT risk posture, our client was also in the middle of migrating one Active Directory into the other. We helped them gain insight into the process by putting the identity data to work and showing them the users that were not migrated yet, the users that had accounts in both Active Directories and so on.
3. Control and Report
In addition to the controls and KPIs, each member with access to Elimity’s identity intelligence platform could personalize its own dashboard, ensuring that only the relevant information was displayed, in a valuable way. With the connectors in place, new identity data was loaded in the platform every day and history was kept for every defined control. This enabled our client to track progress – of both risks and projects – over time and deliver detailed change reports and compelling audit trails.
📎 HOW TO PROVE YOU ARE IN CONTROL
The key identity indicator canvas is an interactive datasheet. In Elimity's guide "How to prove you are in control" we’ll provide you with all the information you need to fill out the datasheet.
-1.png?width=3750&height=1959&name=TEMPLATE%20EBOOK%20(1)-1.png)
👉 8 Categories of identity indicators;
👉 How to choose the right indicators?
👉 Indicators based on the ISO27001-framework;
📎 KPI-Driven approach to Identity & Access Management
Our guide walks you through everything you need
to start using KPIs to improve IAM effectiveness.

