Calculate Your IAM Risks with Free Canvas
A practical template to help you identify, map, and reduce identity-related risk
![[SMART MOCKUP] [GUIDES] [KEY INDICATOR CANVAS]](https://elimity.com/hs-fs/hubfs/%5BSMART%20MOCKUP%5D%20%5BGUIDES%5D%20%5BKEY%20INDICATOR%20CANVAS%5D.png?width=1080&height=1080&name=%5BSMART%20MOCKUP%5D%20%5BGUIDES%5D%20%5BKEY%20INDICATOR%20CANVAS%5D.png) ✅ Example tabs with 8 key KPIs
✅ Example tabs with 8 key KPIs
✅ Use the ready-made template
✅ Based on ISO 27001 and NIS 2
Executive Summary
If you’re responsible for IAM, you know visibility is everything. The Elimity Identity Indicator Canvas helps you quickly map your most important risks—like orphaned accounts, excessive access, and SoD violations—based on proven frameworks like ISO 27001 and NIS 2.
Download the Excel file to:
✅ See 8 key risk indicators in a pre-filled example
✅ Use the ready-made template for your own org
✅ Align IAM efforts with compliance and risk priorities
💡KPI? KRI? KCI?
Key performance indicators (KPIs) measure performance - the achievement of identified goals. Key risk indicators (KRIs) measure risk exposure - they are an early warning to potential threats. Key control indicators (KCIs) measure the effectiveness of controls that are put in place.
One of the main goals of identity management is, however, reducing risk. And the performance of identity management is translated for a large part into the effectiveness of processes, the output. As such, there is not always a clear or strict distinction between a KPI, KRI and KCI within identity management. In this guide, we use the term key identity indicator.
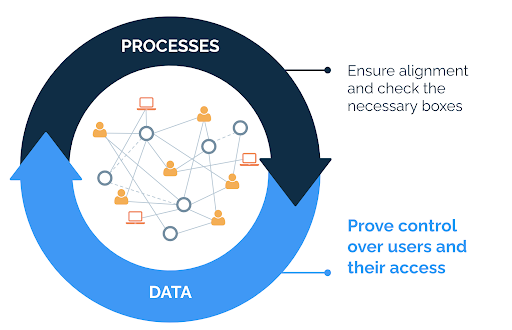
What does it mean to be in control?
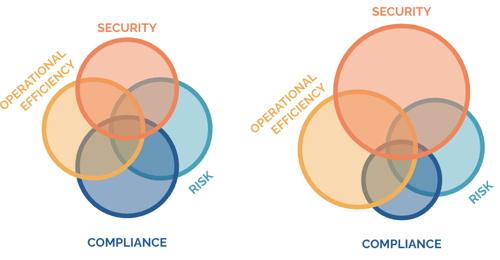
There are 4 aspects of being in control of your identities: security, risk, operational efficiency and compliance. The key identity indicators described next often provide evidence for multiple aspects at once. This is illustrated in the figure below.
The right choice of indicators
For most of the organizations the same set of key identity indicators is relevant. Nevertheless, no two organizations are exactly the same. Depending on their focus areas of being in control, some indicators will be more relevant than others. Answering questions that matter and getting support from management will be much easier if the indicators are aligned with your focus areas.
It’s important to understand that the choice and priority of indicators is not set in stone for all time. There are several factors that could influence what it means to be in control for your organization. Think about strategies and goals that develop over time, more information that becomes available, changes in the regulatory landscape, etcetera.
In the following pages we’ll take a closer look at each of these categories.
1. Orphaned Accounts
What: Accounts that are no longer active or have no owner.
Why: SECURITY + OPERATIONAL EFFICIENCY
Details:
Orphaned accounts form an interesting path for hackers to gain access to organization resources, applications or systems. Organizations that fail to take the necessary steps to close these entry points leave the door on a jar for attackers, and expose themselves to unnecessary risk. By identifying and cleaning up these accounts, security risk is reduced significantly.
Moreover, tracking orphaned accounts can provide insights to improve operational efficiency. When an employee leaves the organization or when a contractor’s project has ended, their accounts must be deactivated (i.e. disabled). This should be part of the typical offboarding process. However, in practice, it happens that those accounts are incorrectly deactivated or not deactivated at all. By finding out why these accounts were not deactivated, the offboarding processes can be improved.
Metrics:
- Accounts for which the user has not logged in for quite some time. Accounts that have not been used for a certain period of time are also known as dormant accounts. What that time period should be exactly can vary for different types of accounts and between organizations. Often 90 days is considered for standard accounts.
- Accounts for which the user has not logged in since they got the account, also called ignored accounts.
- Uncorrelated accounts, also known as ghost accounts. These are accounts that do not belong to any employee or accounts that belong to an employee that is not active anymore. So in other words, accounts without an active owner.
- Accounts with a status indicating inactivity. Think for example about an employment status ‘retired’ or an activity status ‘inactive’. The clue is to look at the user characteristics in the identity system that could indicate inactivity of a user.
👍 Rule of Thumb
A rule of thumb about when an account can be identified as having a high number of roles or permissions: the total number of roles or permissions exceeds twice the average.
Download the full guide to take action yourself!
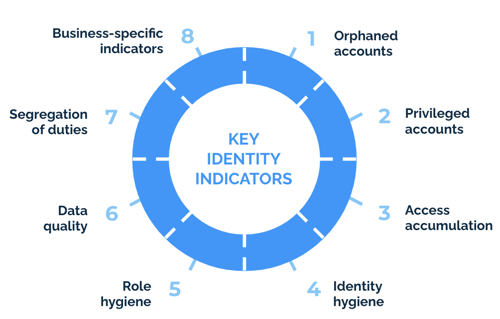
8 Categories of Key Identity Indicators
- Orphaned Accounts
- Privileged Accounts
- Access Accumulation
- Identity Hygiene
- Role Hygiene
- Data Quality
- Segregations of Duties
- Business-specific Indicators
Get our free ebook on how you can level up your B2B SaaS content marketing
Get our free ebook on how you can level up your B2B SaaS content marketing