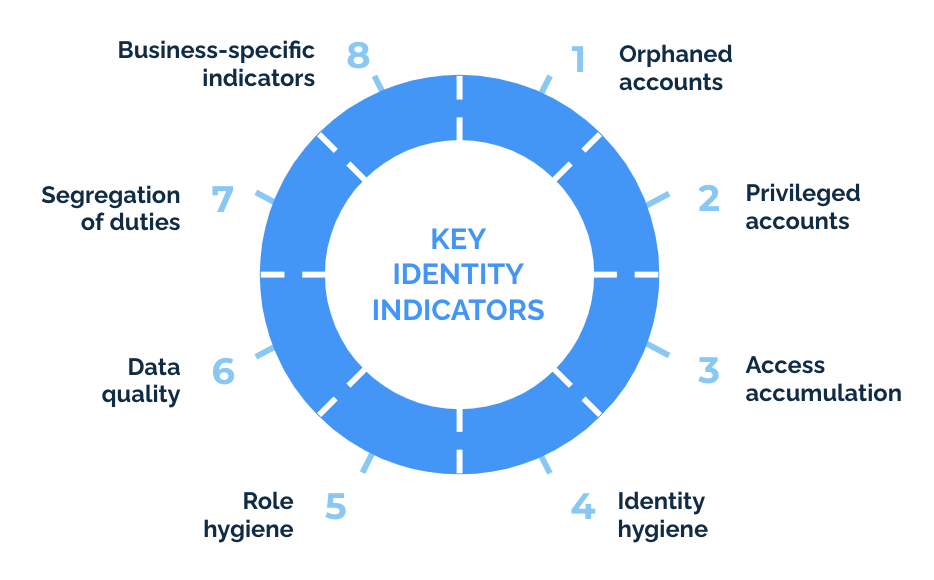
Challenges
- Complex IT Environment: The CISO needed to manage users and access across multiple critical systems, including custom and legacy applications.
- Limited Security Team: The organization's security team was small and couldn't afford a traditional, time-consuming identity governance approach.
- Manual Access Reviews: The security team performed manual access reviews using Excel exports and emails, leading to inefficiency.
- Repetitive Tasks: The security team was burdened with manual and repetitive control tasks related to identity governance.
How Organisations Take Control in a Matter of Days
When facing this kind of challenge, organizations traditionally have two options: they either implement a full stack identity governance solution or they make an inventory of access rights by interviewing people and filling out spreadsheets. We wanted a third option.
Key Results Customer Case
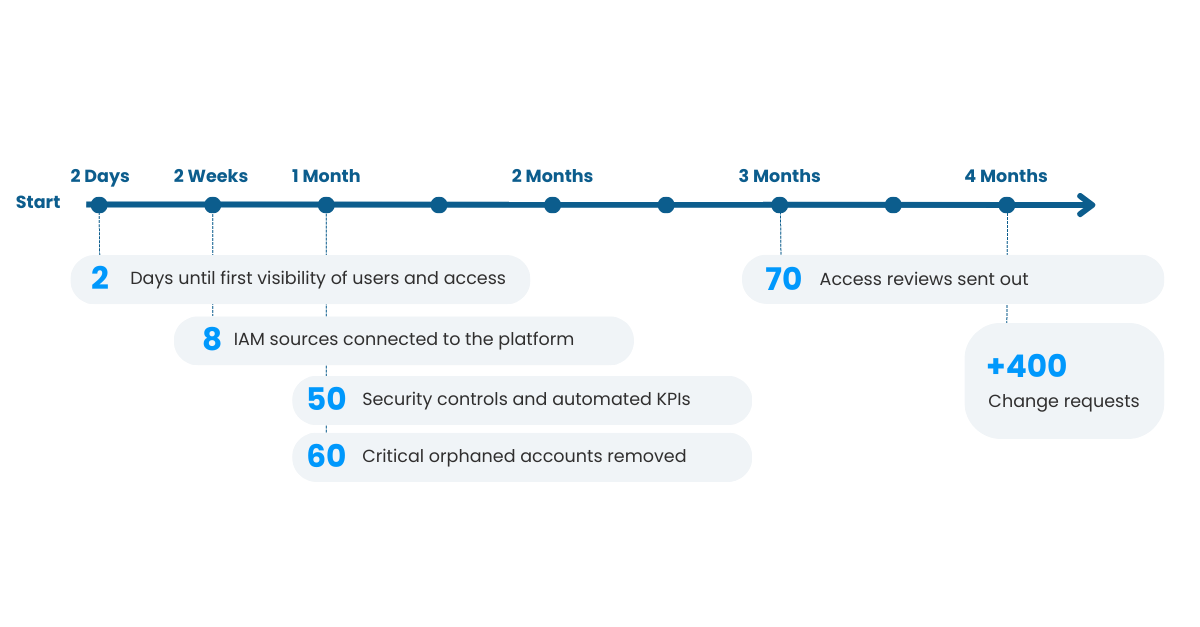
✅ Rapid Visibility: Within 2 days, the company gained visibility into existing users and their accesses.
✅ Comprehensive Data View: Within 2 weeks, an always-up-to-date overview of important IAM data sources was achieved.
✅ Orphaned Account Cleanup: Over 50 critical orphaned accounts, including those belonging to past external contractors, were identified and removed in 1 month.
✅ Automated Monitoring: After 1 month, more than 50 Key Performance Indicators (KPIs) were monitored automatically, addressing various issues.
✅ Access Reviews: Business-friendly and automated access reviews were facilitated for team leaders and application owners.
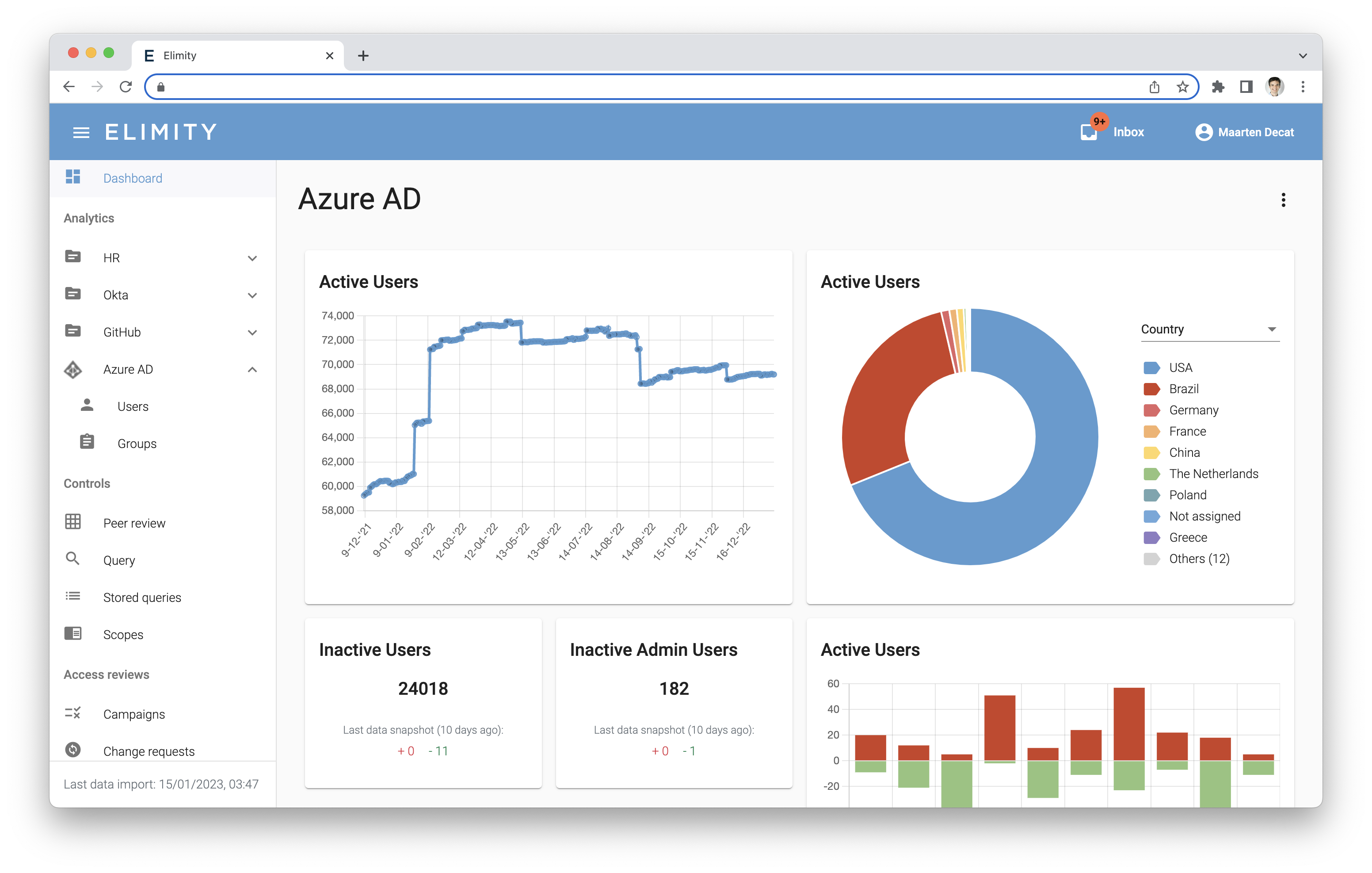
How we applied identity data analytics
☑ Track essential security controls
☑ Ask the business for input through access reviews
☑ Clean up risky accesses
☑ Easily perform identity data analytics
KPI-Driven approach to IAM
Our guide walks you through everything you need to start using KPIs to improve your IAM security.
Your Ultimate IGA-Deployment Checklist
Are you starting your identity governance and administration (IGA) journey? Follow Elimity's checklist for successful IGA deployment.
Insurance company takes control of user access in a matter of days
Download this customer case to learn how a European organization chose Elimity to achieve provable control through lightweight data-drive identity governance.