The NIS Directive is an initiative developed to protect the economy of the EU from major cyberthreats, implying security requirements for companies in EU member states. Let’s take a closer look at the different components of the Directive and the requirements specific to the different sectors in scope.
The importance of the NIS Directive
It was already widely discussed at the Kuppingercole Cybersecurity Leadership Summit 2022 that the NIS Directive provides legal measures to raise the overall level of cybersecurity in the EU. According to a 2022 report from Allianz Global Corporate & Specialty, cyber crime incidents are now estimated to cost the world economy in excess of $1trn a year, which is a significant increase compared to the 2014 figure of $445 billion. Consequently, it’s no surprise that cyber resilience is now regarded as the major ESG risk topic for companies.
But it’s not just regular companies that might get affected by cybercrime. Critical infrastructure systems like power plants, water supply services, financial institutions and military installations are equally threatened. These days, the storyline of Die Hard with a Vengeance – starring Bruce Willis as John McClane –, where bad guys hack their way into power plants, public utilities and traffic systems, doesn’t seem that far-fetched anymore.
How the EU tackles this issue
The European Commission understands all too well that our society and economy heavily relies on ICT and that it’s therefore vital for critical infrastructure systems, digital service providers, as well as other companies to be well protected against cyber threats.
This extract – taken from the actual NIS Directive – clearly expresses the EU’s point of view: “The magnitude, frequency and impact of security incidents are increasing, and represent a major threat to the functioning of network- and information systems. Those systems may also become a target for deliberate harmful actions intended to damage or interrupt the operation of the systems. Such incidents can impede the pursuit of economic activities, generate substantial financial losses, undermine user confidence and cause major damage to the economy of the Union.”
The NIS Directive is an important initiative – actually the first of its kind in Europe – to ensure that protection against cyber threats is properly addressed. It was commissioned by the European Commission and created by the European Union Agency for Network and Information Security (ENISA).
As the EU consists of different countries with different cultures and values, the European Commission didn’t want to impose a single, overarching cyber security standard onto its members. Therefore, every EU-member is enabled to ‘transpose’ the directive – within certain limits, of course – into its own legislation.
The NIS Directive dissected
The main goal of the NIS Directive is to improve the cybersecurity level within the European Union. The directive consists of three components:
1-Improving cybersecurity capabilities at national level
EU-members need to develop strategic objectives, priorities and a governance framework in order to secure their network and information systems. Each member has to designate one or more national competent authorities to monitor the application of the directive. They also need to designate one or more Computer Security Incident Response Teams (CSIRTs). The duties of those CSIRTs – amongst others – is to monitor cybersecurity incidents and provide early warnings.
2-Enhance cross-border collaboration with other EU-members
This collaboration will be put into practice by the NIS Cooperation Group and the Network of National CSIRTs. The NIS Cooperation Group will share best practices, provide guidance assistance to member states, set-up training programs, and so on. The National CSIRTs Network will issue guidelines on operational cooperation and exchange information on CSIRT services and operations.
3-Make sure that operators of essential services (OESs) and digital service providers (DSPs) are supervised on a national level
The NIS Directive states that EU-members need to supervise the cybersecurity of OESs, such as energy (electricity, oil and gas), transport (air, rail, water and road), drinking water supply and distribution, healthcare, banking and credit institutions, financial market infrastructure (trading venues, central counter parties) and digital infrastructure (internet exchange points, domain name system service providers, top level domain name registries).
According to the directive, digital service providers (DSPs) are online marketplaces, cloud computing services and search engines. In short, the directive requires that DSPs take appropriate security measures and notify substantial incidents to the authorities.
Which security requirements are applicable for your sector?
The main goal of the NIS Directive is for companies to meet certain international security standards. For many companies however, it is still very unclear as to what they actually have to do. A lot of businesses aren’t sure what standards and guidelines they have to follow. To help with this issue, ENISA created a guide that describes the different frameworks that can be used for every sector.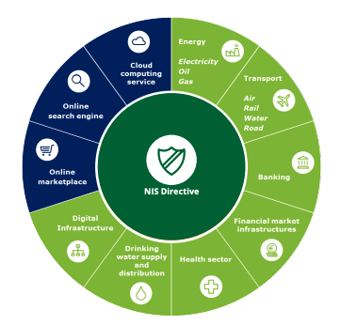
Apart from that, it’s good to know that the NIS Directive in Belgium states that the security policy of organizations that are subject to NIS needs to be in accordance with ISO 27001. This doesn’t mean those organizations need to have an ISO 27001 certification, however. What it does mean, is that the government will demand for audits that are based on the rules as described in ISO 27001.
The link with Identity and Access Management (IAM)
Generally seen, organizations should consider 14 NIS Security Principles with one of them being the “Identity & Access Control”. The latter implies that the organization understands, documents and manages access to networks and information systems and supports the operation of essential functions. Users (or automated functions) that can access data or services are appropriately verified, authenticated and authorized.
PS: Don’t forget to take a look at Elimity Insights, a powerful access governance solution which enables you to stay secure and compliant with regulations like NIS.