More Tools, Less IAM Visibility
In today's complex enterprise environments, organisations face a significant challenge: despite investing in numerous Identity and Access Management (IAM) tools, they frequently encounter bigger blind spots in IAM.
In other words, identities and their access rights are not centrally unified. Instead, identity data ends up scattered across many different systems, including:
- Repositories (e.g., Active Directory, Azure AD, Okta)
- Identity Governance and Administration (IGA) solutions (e.g., SailPoint, Omada, OneIdentity)
- Privileged Access Management (PAM) systems (e.g., CyberArk, Delinea)
- HR platforms (e.g., Workday, SAP, AFAS software)
- Cloud services (e.g., AWS, Google Cloud, Azure)
- SaaS applications (e.g., Office 365, G Suite, GitHub)
- Various databases (e.g. SharePoint, Dropbox, Windows File Shares)
With identity data spread across so many silos, IAM reporting becomes fragmented, integration is limited, and overall visibility into who has access to what is lacking.
%20.png?width=1024&height=512&name=HUBSPOT%20BLOG%20-%20IDENTITY%20DATA%20FABRIC%20(Before)%20.png)
The Impact: Security, Compliance and IAM Gaps
This data chaos manifests in three key areas: security, compliance and IAM teams.
🔐 Security
IAM data chaos leads to security because organizations are not able to identify orphaned accounts, discover privileged accounts, track excessive permissions, or know which retired employees still have access to sensitive data like Windows File Shares.
👉 Download the 8 most important identity security controls here.
🧾 Compliance
IAM data chaos leads to difficulty in proving that all systems have been reviewed, knowing who can access privacy-sensitive folders, or understanding complex role functionalities for audit purposes (e.g. DORA, ISO27001 or NIS2).
🧑💻 IAM Experts
IAM data chaos makes it harder to define appropriate roles, to ensure that all groups have an owner assigned, to label high-privilege accounts, or to resolve synchronisation errors between critical systems like Active Directory and Azure.
Solution: Building an Identity Data Fabric
More tools create bigger blind spots, forcing organisations to adopt a data-first strategy centred on the Identity Data Fabric.
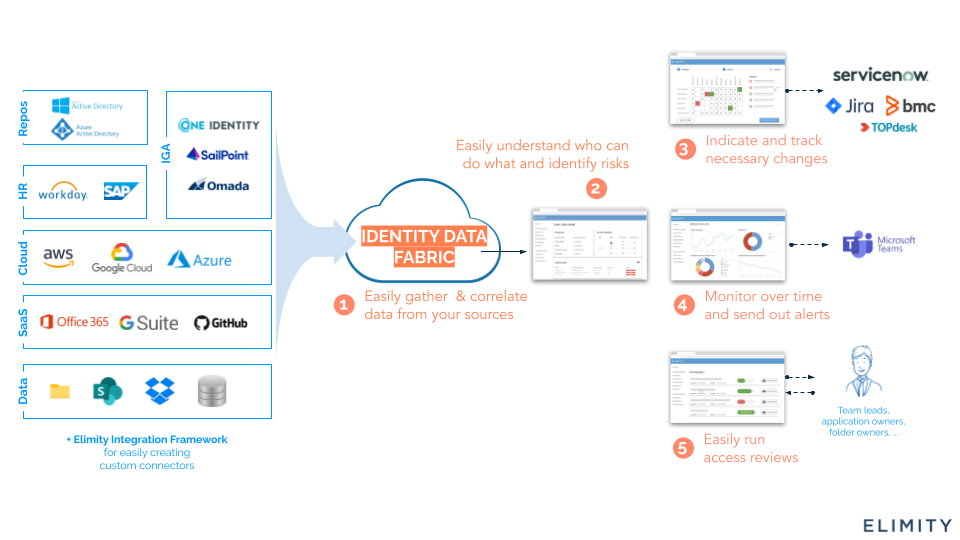
Building an "Identity Data Fabric" involves bringing together the data from your identity silos into a single, overarching identity data graph.
The Identity Data Fabric works to collect, link, analyse, present, share, and monitor identity data, building a data-centric fabric or mesh across systems that were previously isolated.
.png?width=1024&height=512&name=HUBSPOT%20BLOG%20-%20IDENTITY%20DATA%20FABRIC%20-%20ARCHITECTURE%20%20(1).png)
Benefits: From IAM Sprawl to Visibility
By establishing a robust, integrated IAM data foundation, the Identity Data Fabric empowers organizations to collect, link, analyse, present, share, and continuously monitor identity data across all sources.
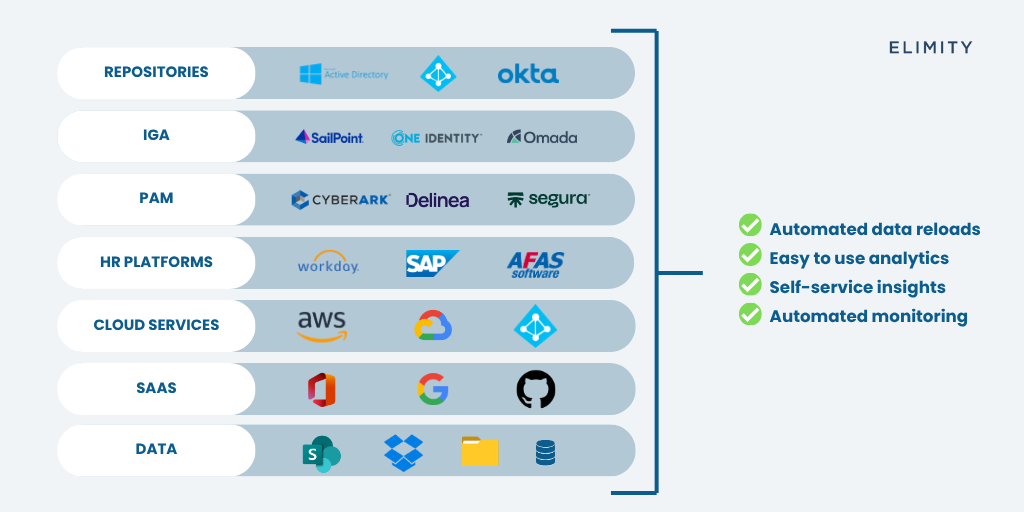
This results in the following benefits
- Automated data reloads: Always work with the latest data, no manual exports
- Easy to use analytics: Analyse access and risk visually, no coding required
- Self-service insights: Empower IAM and security teams with on-demand answers
- Automated monitoring: Identify violations and anomalies before they become incidents
Must-Haves for Identity Data Platform
To achieve this, a proper Identity Data Fabric platform should come with the following features:
-
Out-of-the-box IAM connectors – Instantly plug into AD, Azure AD, PAM and IGA.
-
Out-of-the-box IAM security controls – Start with proven identity security controls
-
IAM-specific analyses – Drill into privileged accounts, orphaned users, and much more
-
Secure data sharing – Collaborate safely with stakeholders across IT, audit, and business
-
Indicate necessary changes – Know what needs to change—and where to act
-
Streamlined access reviews – Make access governance efficient, auditable, and business-friendly
Real-world Use Cases
An Identity Data Fabric is a versatile approach with many different use cases in practice. These are some of the more common use cases:
- Risk Analysis & Clean-Up
Quickly identify and prioritise high-risk items like orphaned or privileged accounts to reduce cyber risk.
- Data-Driven Identity Governance
Achieve data-driven governance by building a central view of users and permissions, reviewing access, and continuously monitoring to ensure compliance and control.
- Self-Service Identity Analytics
Provide a self-service identity intelligence platform, enabling IAM analysts, security analysts, and other professionals with data analytics to improve decision-making and engagement.
- Automated Role Mining
Structure access rights, deliver insights, and generate initial role models quickly to prove compliance.
👉 Learn how this Fortune 500 bank empowers its IAM Professionals

Final Takeaway: Make Data the Core of Your IAM Strategy
To move from identity chaos to control, your IAM strategy must start with data.
-
Unify fragmented identity sources into a single, connected identity data graph.
-
Gain clear visibility into who has access to what, across systems.
-
Focus on high-impact use cases, such as risk remediation, lightweight governance, policy modelling, or automated role mining.
-
Avoid manual data work; go for a dedicated platform.
💡 Tip: We've seen the greatest impact at our customers when their Identity Data Fabric includes the following key sources:
- Repositories - Active Directory, Azure AD, Okta
- Identity Governance and Administration (IGA) solutions - SailPoint, Omada, OneIdentity
- Privileged Access Management (PAM) systems - Segura, CyberArk, Delinea
- HR platforms (e.g., Workday, SAP, AFAS software
- Cloud services (e.g., AWS, Google Cloud, Azure AD
- SaaS applications (e.g., Office 365, G Suite, GitHub
- Various databases (e.g. SharePoint, Dropbox, Windows File Shares
👉 Interested in seeing how other organisations built an identity data fabric?
.png?width=1280&height=720&name=PRODUCT%20TOUR%20-%20HOME%20PAGE%20-%20WHITE%20BACKGROUND%20%20(1).png)