Improve ROI of your IGA with Identity Data Analytics
When having an Identity Governance and Administration solution (IGA) in place, you expect the reporting and analytics to come from this system. But traditional approaches often fall short in answering the growing list of data questions related to IAM.
✅ IGA Reporting: The Typical Challenges
✅ What is Integrated Identity Analytics?
✅ Customer Cases: How create IAM reports with Identity Analytics
✅ Demo Integrated Identity Analytics
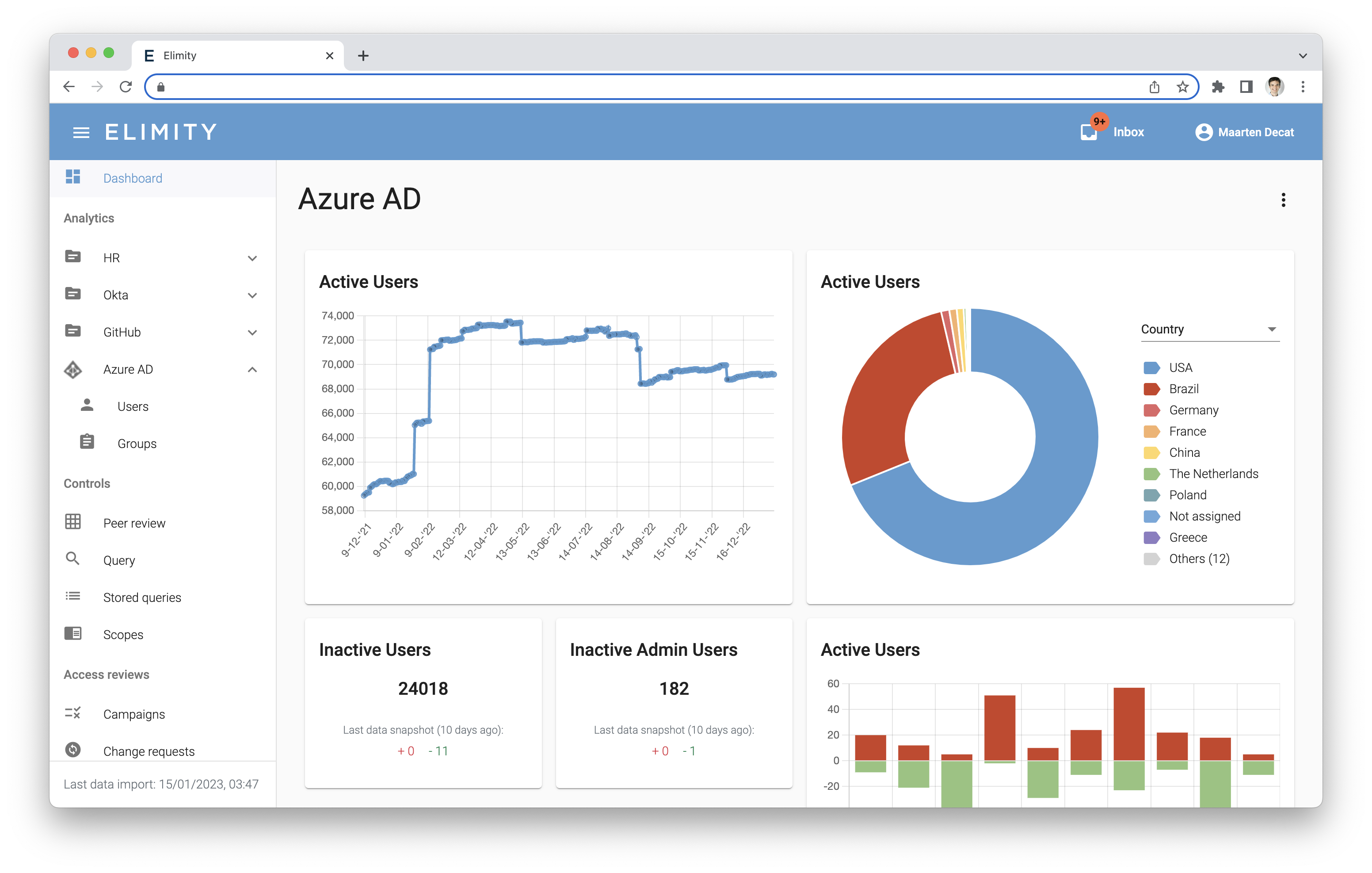
.png)
Do You Recognize These IAM Challenges?
1️⃣ Reporting capabilities and analytics of existing IGA are limited
2️⃣ Building a data lake for all IGA reporting requirements
3️⃣ Spending months on reporting from your IGA database
4️⃣ Performing manual identity data investigations
5️⃣ +50 employees work on a daily basis with multiple Active Directories





The 8 Most Frequently Used KPIs to Test Your IGA
Identifying 'Identity and Access' inefficiencies or gaps remain a challenge for organisations with numerous applications and valuable data.
Our guide walks you through everything you need to start using KPIs to improve IAM effectiveness.
How we applied identity data analytics
- Deployed Elimity Insights platform
- Integrating with 10+ applications
- Linked all data, ensuring up-to-date identity data set
- Empowered IAM team with day-to-day analyses
- Advanced data insights
“Elimity's platform provided crucial insights regarding the security of our IT assets. Even more important, it allowed us to share the responsibility of user access with the business units."

“Monitoring user access to our organisation’s data used to be done manually. Elimity’s platform automated this process, as well as reports on the risks and controls in place, saving our security team valuable time."







