
Download Solution Brief
Learn how Elimity enables organizations to eliminate identity and access risks for everything they use.
Read how Elimity insights:
✅ Collects Data
✅ Creates Identity Visibility
✅ Reviews and Cleans Up
✅ Monitors and Alerts
✅ Role Mining
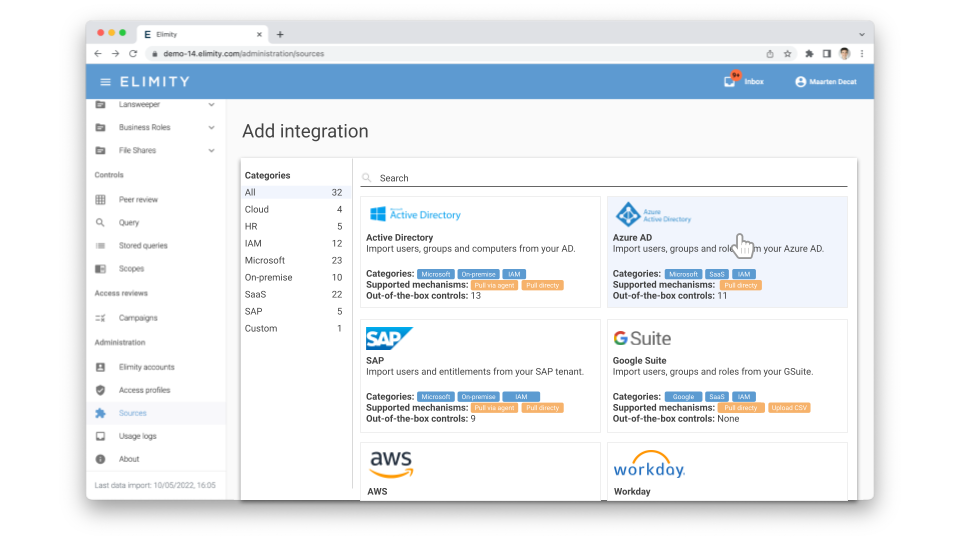
Out-of-the-box Connectors
- Get up and running in minutes with out-of-the-box connectors
- Integrate your hybrid environment with direct connections for SaaS applications and local agents for on-premise applications.
Gain valuable insights relying on Advanced Analytics
Instead of performing controls manually, and thus periodically, be in control continuously with Elimity’s identity and access risks and controls.



Monitoring user access over time
Save time reporting on access management with Elimity’s automated reports, enabling you to follow-up on the most important identity controls for your organization, track progress over time, and gather compliance evidence.
Comply with the highest security standards and leverage your cyber maturity to your clients during RFP processes.
Large organization speeds up and de-risks deployment of a new IGA suite
Download this customer case to learn how a large governmental organization uses Elimity to speed up the multi-year transition from a homegrown access management system to a full-fledged IGA.
Previously, it took our IAM team up to 3 weeks to complete the peer review within the organisation. Since implementing the Elimity platform, the process has become just one click away, reducing the workload for the team significantly.
Results Customer Case
✅ Achieve visibility of existing users and access within 2 days
✅ Get up-to-date overview of +10 IAM sources within 2 weeks
✅ Set up user-friendly self-service analytics for IAM stakeholders
✅ Identity analytics used in several projects, including role design
✅ Automated monitoring of KPIs over time






