Protecting your IT assets in one place
Our advanced platform provides complete visibility in your applications and users, allowing organizations to comply with highest security standards.

Collect. Visualise. Act. Repeat.
Ensuring the right identities get the right access to the right access in the most efficient manner.
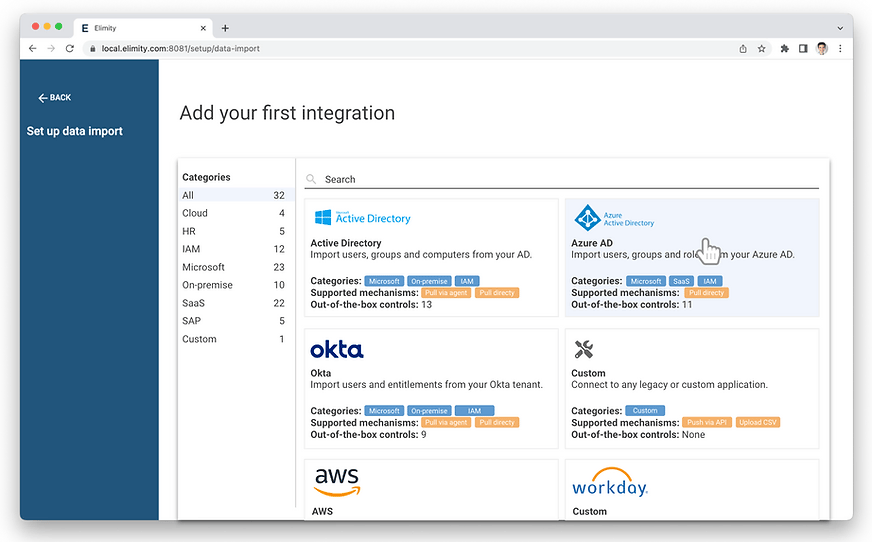
Out-of-the-box Connectors
Get up and running in minutes with out-of-the-box connectors, built with the principle of least privilege in mind, requesting read-only access and only on the metadata required. Integrate your hybrid environment with direct connections for SaaS applications and local agents for on-premise applications.
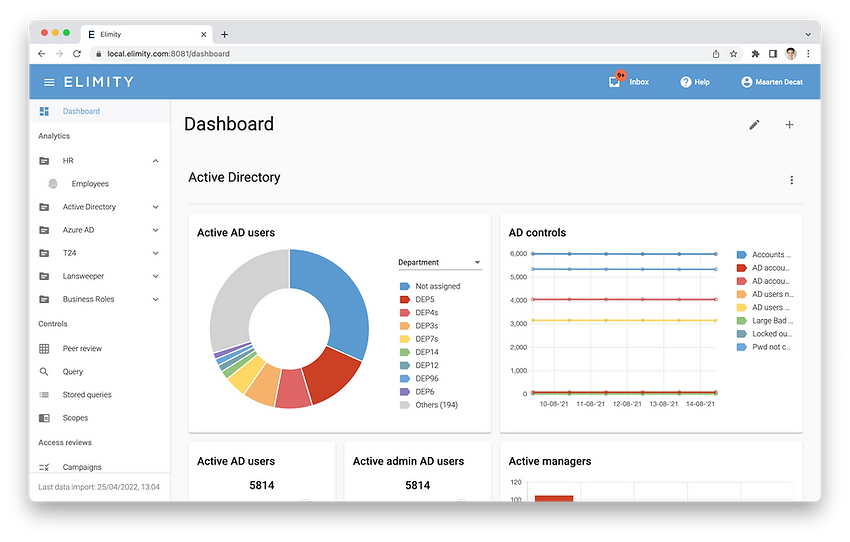
Gain valuable insights relying on Advanced Analytics
Instead of performing controls manually, and thus periodically, be in control continuously with Elimity’s identity and access risks and controls.
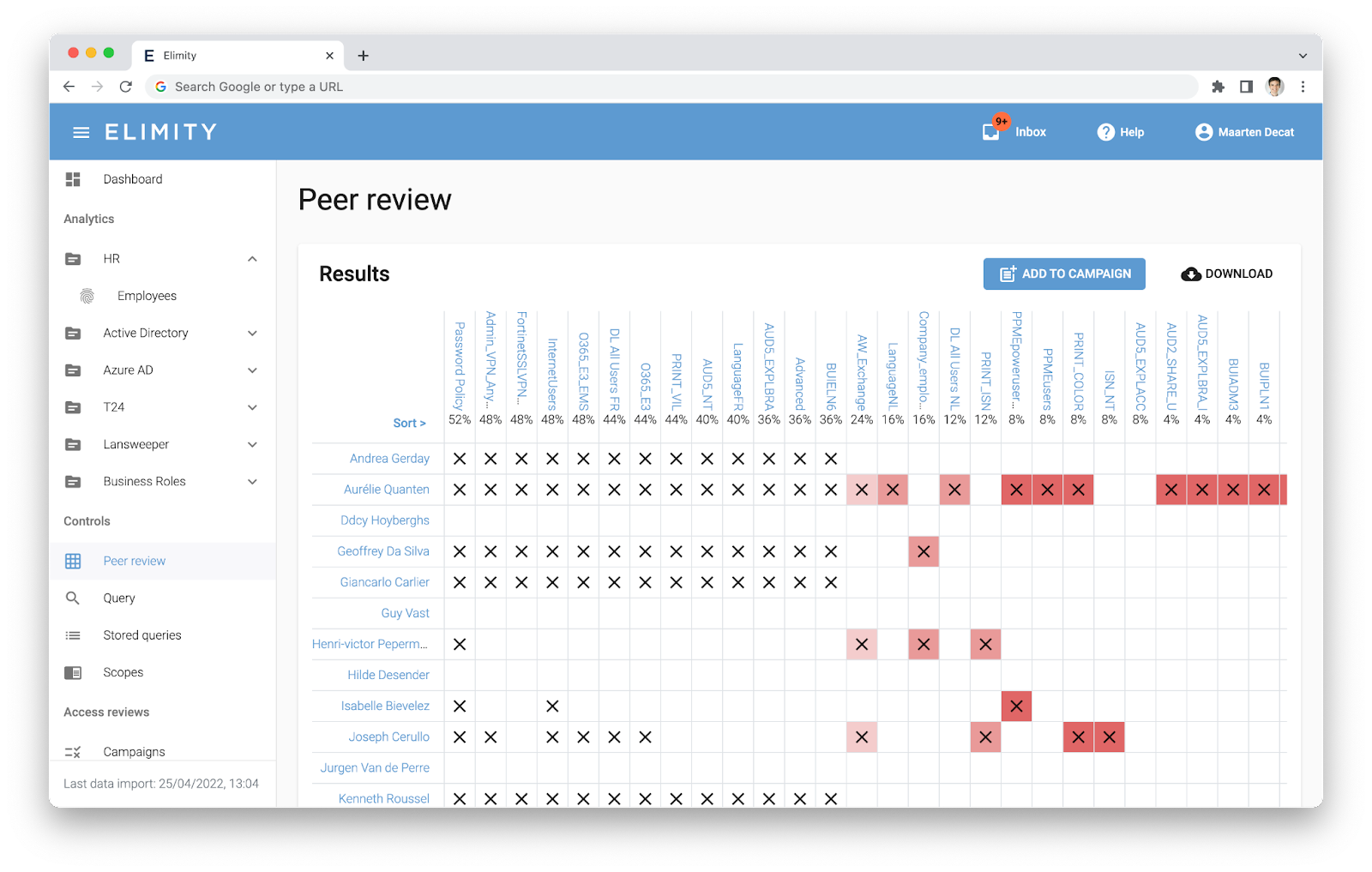
Dedicated visual identity analytics such as peer and pattern analyses enable you to query and present data so you can make informed decisions, not just see numbers. Discover relations, unravel anomalies or spot unknown patterns with our built-in powerful algorithms.

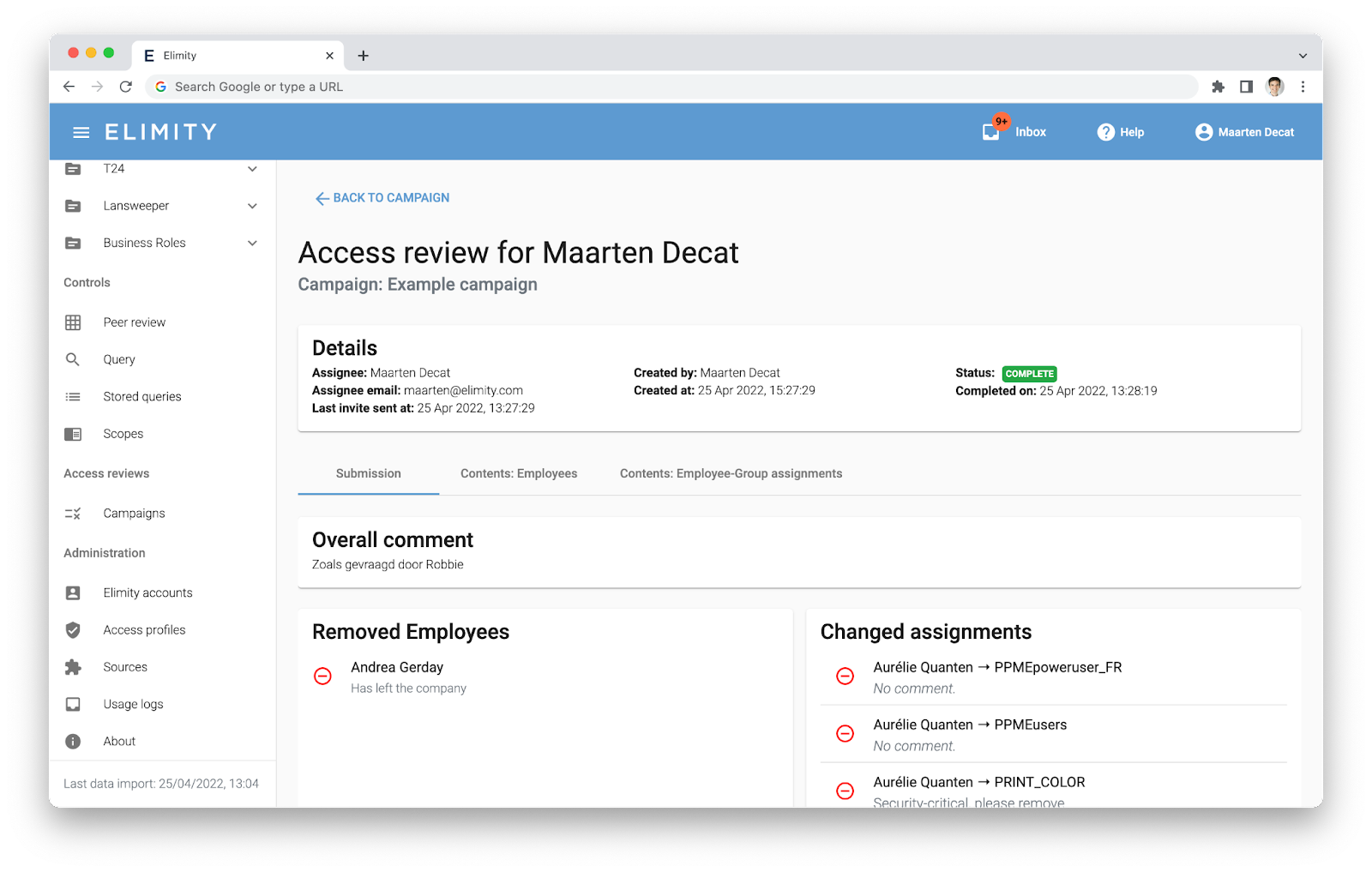
Monitoring user access over time
Save time reporting on access management with Elimity’s automated reports, enabling you to follow-up on the most important identity controls for your organization, track progress over time, and gather compliance evidence.
Comply with the highest security standards and leverage your cyber maturity to your clients during RFP processes.
Make access management a shared responsibility
Give your identity experts, application owners and role owners the information they need to take well-founded access decisions by democratizing identity insights. Easily slice and dice your identity data, understand relationships and assess the impact of changes.