MICROSOFT ACTIVE DIRECTORY - IDENTITY CONTROLS GUIDE
Understanding the relationships between people, access and data is crucial. In this guide, we bundled the identity controls that apply to Microsoft Active Directory. Moreover, this set of controls has proven to be applicable to the majority of the organisations.
![[SMART MOCKUP] [GUIDES] [MICROSOFT AD - The Essential Set of Identity Controls]](https://elimity.com/hs-fs/hubfs/%5BSMART%20MOCKUP%5D%20%5BGUIDES%5D%20%5BMICROSOFT%20AD%20-%20The%20Essential%20Set%20of%20Identity%20Controls%5D.png?width=1080&height=1080&name=%5BSMART%20MOCKUP%5D%20%5BGUIDES%5D%20%5BMICROSOFT%20AD%20-%20The%20Essential%20Set%20of%20Identity%20Controls%5D.png)
✔️ The eight building blocks of AD;
✔️ Overview of comprehensive security controls
✔️ For all organizations using AD;
Introduction
In a business and IT context, there’s only one constant: change. Think of hybrid IT landscapes that keep on evolving, tens or even hundreds of systems and applications that need updates on a regular base, a growing number of temporary contractors such as freelancers and consultants, etc. Considering this pace of change, maintaining an overview of the situation has become more challenging than ever. But if you can’t see all the users across your IT environment and if you don’t know what applications and data each of those users can access, it is close to impossible to control risks and prevent threats.
Understanding the relationships between people, access and data is a crucial factor in this regard. In other words: getting to know the unknowns. In this guide, we bundled the identity controls that apply to Active Directory. Moreover, this set of controls has proven to be applicable to the majority of the organisations. In the ebook ‘How to build the perfect risk cockpit for Microsoft Active Directory’ we discussed the six steps to set up comprehensive and scalable risk cockpit.
In this guide, we’ll elaborate on the eight building blocks of such a cockpit. Implementing these controls will help you to uncover all the unknowns. Because you can’t protect what can’t see.
This guide is written for IAM, IT and security professionals. The contents are not limited to any organizational size, structure or industry. The premise is, however, that the organization uses Active Directory. Nevertheless, most of the controls also apply to other applications albeit with some adjustments.
💡Additional information and insights
👉 Tips & tricks
💻 Screenshots and explanation about Elimity Insights
Control Sets
You can improve the overall security health of your Active Directory by identifying, analyzing and responding to risks and potential threats. On the following pages, we provide you a comprehensive collection of controls, which has proven to be useful for the majority of organizations.
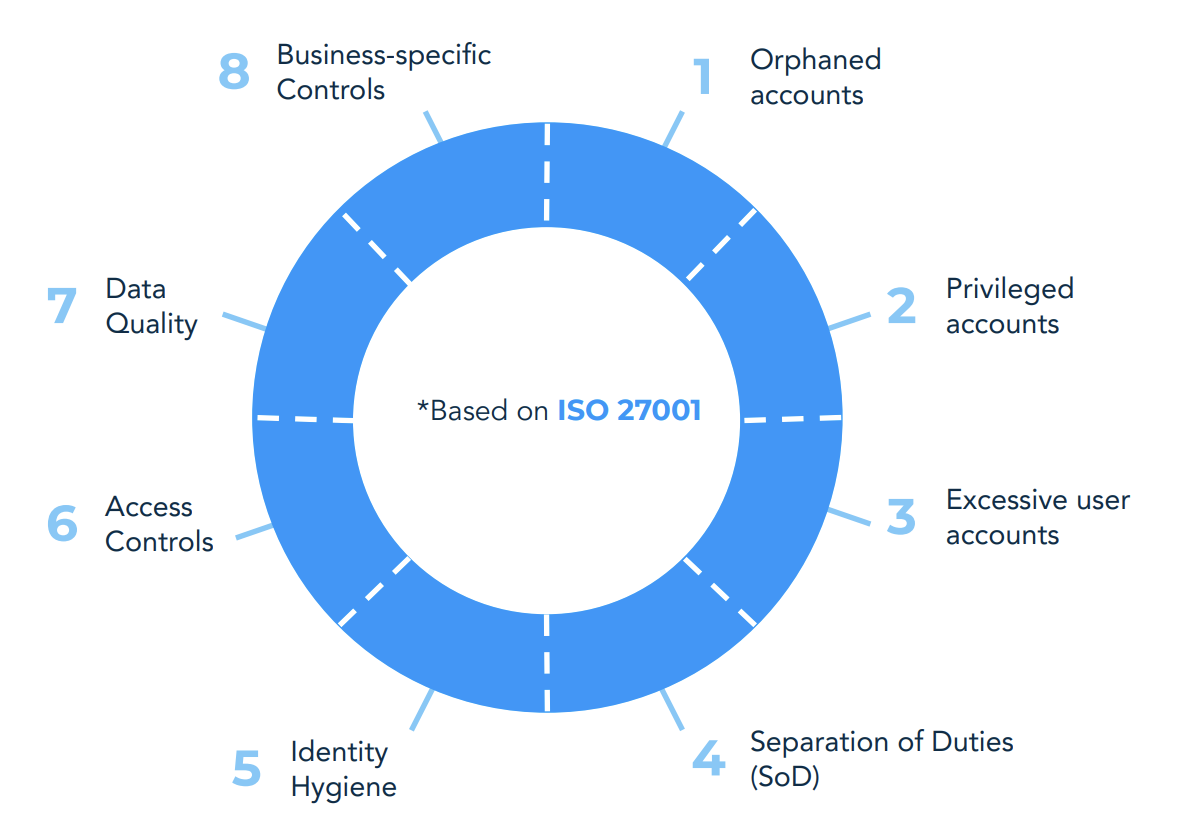
Each of those control sets includes several specific security controls. You can extend or limit this set of controls according to the security standards you want to comply with and to the business-specific context you are working in.
The ISO 27001 based identity wheel (see on the right) shows eight control sets that are applicable for the majority of modern organizations. On the following pages, these control sets are explained in more detail..
💡 Elimity Insights
Within identity management, an ‘outlier’ can be understood as someone (or something) that has more access rights than necessary. One - quite intuitive - method to detect outliers is by comparing their access rights to those of their peers. Think about scenarios such as team member that should have similar access rights (i.e. belong to the same groups). Elimity Insights visualizes these kind of situations in an easy-to-digest matrix and automatically colour codes potential outliers.
This automated risk indication enables you to detect outliers in no time. In the figure it can easily be seen that Bellanca Supat is the only one who is assigned a cer
Resources and frameworks for your IAM journey
Free documentation designed to help IT and Security professionals tackle their daily security challenges in the continuously changing IT landscape.