Example of an Identity Security Assessment Report
Have a look at a final report of an identity security assessment, provided to an European customer. The report includes comprehensive reporting on the main identity risks, delivered within days.
.png?width=940&height=788&name=SMART%20MOCKUP%20-%20IDENTITY%20SECURITY%20REPORT%20(1).png)
✅ +120 Identity Security Controls
✅ Example from actual customer
✅ NIS 2-Framework
Download the report here
What is an Identity Security Assessment?
Elimity provides security teams with a one-time analysis of your users and their accesses with comprehensive reporting on identity risks, ensuring NIS 2 and ISO 27001 certification proof, and delivered in just two weeks.
✅ One-time analysis of your users and access
✅ Identify your top identity risks
✅ NIS 2 and ISO 27001 certification proof
✅ 2-week access to all features
Executive Summary
Securing access to data and applications has become a cornerstone of any modern cybersecurity strategy, especially in light of evolving regulations such as the NIS2 Directive.
However, traditional user access governance projects have often involved multi-year rollouts and the need for specialized personnel, leading many companies to shy away from them, leaving themselves vulnerable to excessive risk.
For these organizations, a lightweight approach to user access governance can provide the solution. This method streamlines access governance by focusing on the essentials: minimal data collection, user-friendly risk analytics, simplified access reviews, and easy integration into existing ITSM processes.
This is why we are launching the Identity Security Assessment—a quick, efficient way for companies to gain control over access governance.
Introducing Elimity's Identity Security Assessment
The 'Identity Security Assessment' is one-time analysis of your users and their accesses, identifying your top identity risk and ensuring NIS2 and ISO 27001 certification compliance. Delivered within just two weeks!
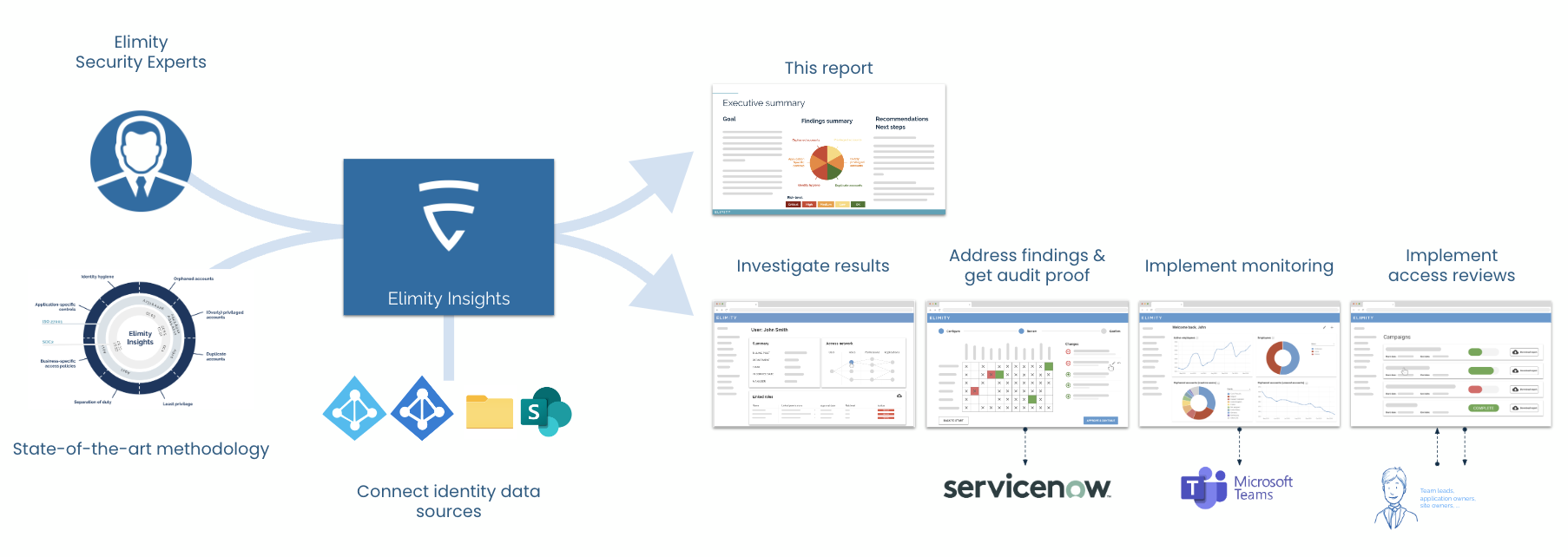
(1) Data Collection:
Your critical system data is securely loaded into Elimity Insights, a state-of-the-art platform for identity security analysis.
(2) Risk Analysis:
Elimity’s security experts analyze the data, identifying identity-related security risks and access vulnerabilities.
(3) Comprehensive Report:
The findings are summarized in a clear, actionable report, highlighting key security gaps and offering recommendations for improvement.
(4) Ongoing Insights:
Following the report, you have two options:
- One-time report: Use the insights to take immediate action on the findings.
- Licensing Elimity Insights: Continue using the platform to address the findings, implement continuous monitoring, and streamline access governance processes over time.
What you get during the Identity Security Assessment
✔️ Instant Visibility into Users and Groups
✔️ +50 Identity Controls for Mature Governance
✔️ Set Up and Delivery in 2 Weeks, Not Months
✔️ NIS2 and ISO27001 Compliance Proof
✔️ Access to All Elimity Features
.png?width=300&height=169&name=Computer%20Screens%20(6).png)
