User Access Screening
Our client, active in the manufacturing industry wanted insights in its current IT risk posture, but faced multiple challenges:
- Limited control over users and accounts
- No view on user access and its risks
- No risk metrics
Elimity performed an in-depth analysis of the key access risks residing in and across their most important applications
Key insights and findings in less than 3 days.
💡 User Access Screening?
As so many organizations, our client, active in the manufacturing industry, wanted insights in its current IT risk posture.
They knew they had too little control over the accounts and their accesses, but had no comprehensive overview of the situation. As a result, they didn’t know exactly what the situation was and where the biggest risks were located. That, in turn, kept them from convincing management to free up resources in order to take action.
To help the client, we performed an in-depth analysis of the key access risks residing in and across their most important applications, and provided them with a report including our findings and recommendations. In just 3 days of work, this enabled them to understand their access risks and gave them objective numbers to support decision-making with regard to next steps.
We provided our client with a detailed report of the key access risks in just a couple of days and gave them access to our platform so they could dig a little deeper into the results themselves.
Using technology to perform an in-depth analysis gave our client the insights they needed to understand their access risks and enabled them to let others understand them as well.
They used these insights to support the development of the identity roadmap. First stop: clean-up to improve the IT risk posture.
APPROACH
We provided our client with a detailed report of the key access risks in just a couple of days and gave them access to our platform so they could dig a little deeper into the results themselves.
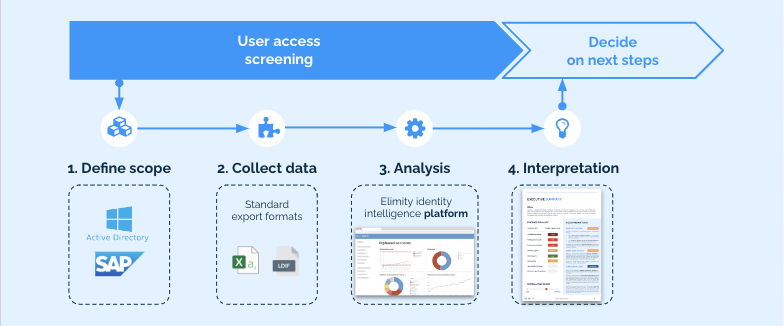
1. Focus on actual risk
As opposed to typical IAM assessments, we don't focus on the presence of governance processes, but on the actual IT risk present in the existing accounts and their accesses. This allows the customer to prioritize clean-up efforts for maximal risk reduction and efficiently introduce governance processes later on.
2. Data-driven
We put identity and access data to work with our dedicated technology allowing for a more cost-efficient but also more in-depth analysis of the IT risk posture.
3. Non-invasive
We conduct the screening without impacting operational systems. There’s no need to deploy agents or make changes to the infrastructure.
📎 HOW TO PROVE YOU ARE IN CONTROL
The key identity indicator canvas is an interactive datasheet. In Elimity's guide "How to prove you are in control" we’ll provide you with all the information you need to fill out the datasheet.
-1.png?width=3750&height=1959&name=TEMPLATE%20EBOOK%20(1)-1.png)
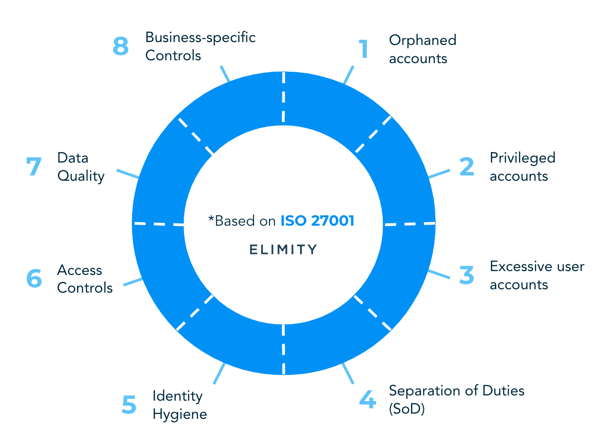
👉 8 Categories of identity indicators;
👉 How to choose the right indicators?
👉 Indicators based on the ISO27001-framework;
📎 KPI-Driven approach to Identity & Access Management
Our guide walks you through everything you need
to start using KPIs to improve IAM effectiveness.

