✅ Pain-Free Access Recertifications
How this CISO replaced Excel and Email with Automated Access Reviews
✅ Pain-Free Access Recertifications
Get the free guide!
Executive Summary
Manual access reviews are no longer scalable or secure. This customer case details how a CISO at a global manufacturer replaced outdated Excel and email-based reviews with Elimity’s automated platform.
The result: enhanced security, streamlined compliance, and governance at a fraction of the cost of a full IGA deployment.
What are access reviews, and why are they important?

User access reviews are routine checks to confirm that employees have the right access to data, systems, and applications. These reviews ensure that only the necessary people have access to sensitive information.
They help businesses maintain security by reducing the risk of unauthorized access, ensuring compliance with cybersecurity regulations.
Many organizations still rely on manual processes like exporting data into Excel sheets, sending emails to team leaders, and manually tracking progress. While this approach might work, it creates a number of significant issues:
- Manual Data Collection: Highly skilled engineers waste time collecting data from multiple systems, often based on outdated information.
- Outdated and Unreliable Excel-Based Processes: Manual data entry, slicing Excel sheets, and macros increase the risk of errors.
- Lack of Progress Tracking: Without proper tools, tracking and reminding reviewers becomes a tedious, full-time job.
- Manual Follow-Up: Converting feedback into ITSM tickets requires more manual effort, causing delays and inefficiencies.
Why manual processes to review user access fall short?
Manual access reviews, especially using Excel, lead to high overhead, limited scalability, and the tendency to focus only on core systems. This reactive approach is not business-friendly, introduces inefficiencies, and makes it harder to comply with modern security standards and audit requirements.
Introducing automated access reviews with Elimity
Elimity provides a seamless solution that removes the pain of manual access reviews. Our platform is designed to replace outdated Excel sheets and email workflows with automated, visual, and business-friendly user access reviews.
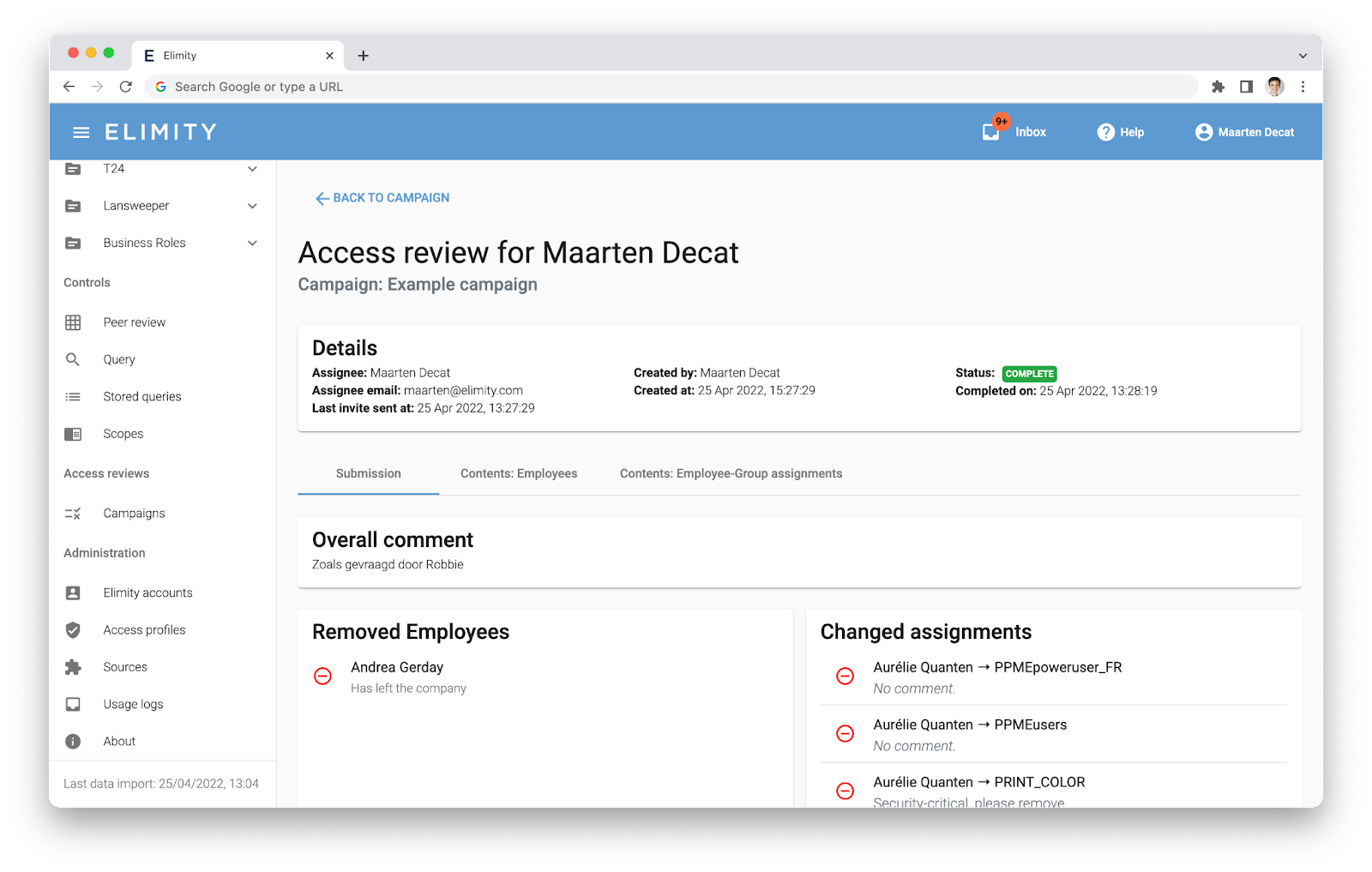
Pain-free access recertifications
Elimity makes access recertifications easy by offering a visual, user-friendly interface where reviewers can quickly identify outliers and recommend changes. No more endless Excel sheets—everything is simplified and centralized in one place.
- Manual Data Collection: Highly skilled engineers waste time collecting data from multiple systems, often based on outdated information.
- Outdated and Unreliable Excel-Based Processes: Manual data entry, slicing Excel sheets, and macros increase the risk of errors.
- Lack of Progress Tracking: Without proper tools, tracking and reminding reviewers becomes a full-time job.
- Manual Follow-Up: Converting feedback into ITSM tickets requires more manual effort, causing delays and inefficiencies.
Business-friendly access reviews
With Elimity, you no longer need a full-time employee to manually track progress. Our automated solution allows you to follow up on each reviewer and campaign effortlessly. You’ll know exactly when a review starts, what’s been completed, and which changes were made—ensuring your audit proof is always available.
Get the audit proof you need
Show internal and external auditors which campaigns were completed, when they were started and completed, and the resulting changes. Elimity gives you all the information you need.
Automated ITSM ticketing
Stop wasting time manually creating ITSM tickets from feedback. Once an access recertification is completed in Elimity, our system automatically generates tickets in your ITSM platform, eliminating yet another manual task from your workload.
Access reviews for any data
Whether you need to review Active Directory groups, folder access, cloud roles, or any other system, Elimity’s flexible API and out-of-the-box connectors make it easy to create campaigns for the data that matters to you.
Take Control of Your Users and Their Accesses

KPI-Driven approach to Identity & Access Management
Our guide walks you through everything you need to start using KPIs to improve IAM effectiveness.
✅ 8 Essential KPIs
✅ Based on ISO27001 framework
✅ Increasing IAM Effectiveness







![[SMART MOCKUP] [GUIDES] [KPI GUIDE WITHOUT BACKGROUND]](https://elimity.com/hubfs/%5BSMART%20MOCKUP%5D%20%5BGUIDES%5D%20%5BKPI%20GUIDE%20WITHOUT%20BACKGROUND%5D.png)